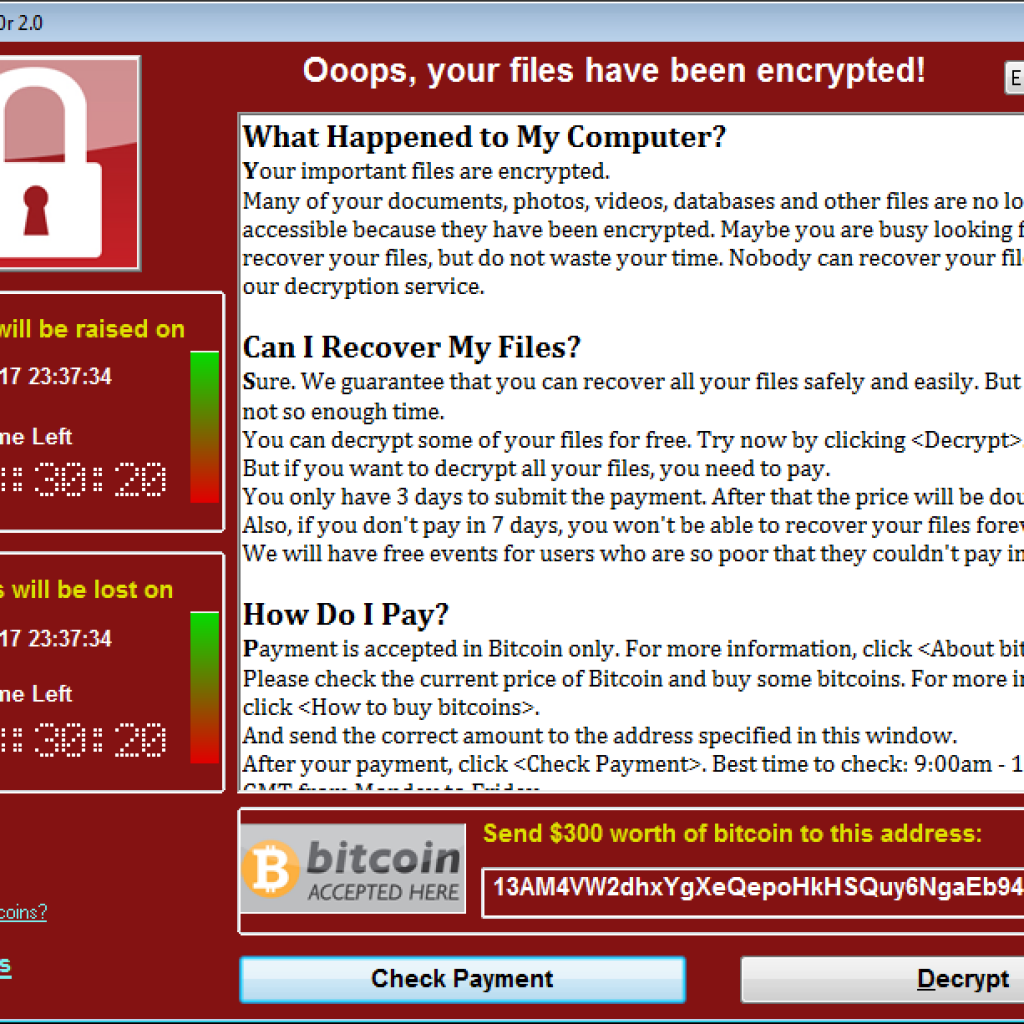
What is WannaCrypt?
WannaCrypt is a ransomware, meaning that it will encrypt your files and ask you to pay, in this case in bitcoins, to decrypt your files. It is important to understand that there is no guarantee that your files will be decrypted even if you pay. The first instances of this attack were reported on Friday, May 12th, 2017 and are still ongoing, although the initial version was stopped, thanks to the actions of a British security researcher.
It spreads by using a vulnerability in the Windows SMB protocol, known as ETERNALBLUE, which was patched in March 2017 (ref: MS17-010). This vulnerability exists only in unpatched Windows 7, Windows Server 2008 and older versions of Windows, such as XP, Vista, etc.
The impressive amount of computers affected by this ransomware means that there is a large number of users and companies who did not update their systems or were using an older version of Windows.
Why is WannaCrypt so dangerous?
Unlike other ransomwares, WannaCrypt uses an SMB vulnerability, which means it does not need any interaction with the user to infect the computer, making WannaCrypt a really threatening ransomware. While WannaCrypt was slowed down, we cannot know if other versions of the malware will surface, with potential new spreading methods. This is why it is imperative to patch any venerable systems as soon as possible.
Am I vulnerable?
WannaCrypt cannot spread to Windows 10 computers by using the ETERNALBLUE vulnerability.
Note that the threat is still under investigation and still active. There is a possibility that the attacker could modify the malware and release a new version which could include new spreading capabilities. Always keep your computer up-to-date and beware of phishing emails.
If you are using Windows 7, Windows Server 2008 or any other older versions of Windows, you are vulnerable if you did not apply the MS17-010 update, which was released on March 14th, 2017 and if you have an exposed SMB. If this is the case, make sure to update your systems as soon as possible.
How can I protect myself?
The best way to protect yourself is to keep your systems up-to-date. As mentioned, an up-to-date computer is not vulnerable to WannaCrypt current spreading methods. Installing the MS17-010 update or using Windows 10 is the best way to avoid this attack.
If you are using an unsupported version of Windows, such as Windows XP, Vista, or Windows Server 2003/2008, Microsoft released an emergency patch (http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598).
- Perform Backups
Ensure that you have a copy of all your important files on a separate hard drive or in the cloud. In the case where you would get infected, you could then retrieve all your files without paying the ransom.
- Disable SMB
SMB1 is enabled by default on Windows, but it can be disabled. Disabling SMB would prevent WannaCrypt to use ETERNABLUE and to infect your computer. You can disable SMB1 by following the instructions in this video: https://www.youtube.com/watch?v=-lE-v60AzUw, which are summed up in the following image:
How to disable SMB1: Taken from YouTube video: “How to Disable SMB to Prevent Against WannaCry Attacks” from HatimTech
- Block SMB ports and use a firewall
If you need to keep SMB1 enabled, you can modify your firewall configurations to block access to SMB ports over the Internet. The ports that need to be blocked are: TCP ports 137, 139, and 445 (port currently exploited), as well as UDP ports 137 and 138.). However, the ideal method for preventing an infection is updating your computer with the latest patches.
- Beware of phishing emails
As mentioned, WannaCrypt has been slowed down, but new versions could be released, including new spreading methods. This recommendation is valid for all similar situations, not just the one at hand.
Technical information
WannaCrypt was created with two major components:
- The ransomware itself, which will encrypt your files;
- The spreading component, which will attempt to exploit the SMB vulnerability (ETERNALBLUE) on other computers within your network to infect them with WannaCrypt.
Once infected, the first action taken by the ransomware is to try to spread to other computers within the network by using the SMB vulnerability. The exploit first sends a special packet to an SMBv1 server and executes itself. It also installs a back door called “DoublePulsar” which can give high a privilege access to the attacker(s).
After the spreading phase, the encryption part begins by searching for specific file extensions to encrypt such as: doc, docx, xls, xlsx, bmp, zip, txt, png, and others. The malware then encrypts them and appends .WNCRY to the filename. It also create a file named “@Please_Read_Me@.txt” in every folder where files are encrypted. That file contains the ransom message. Once the encryption process is complete, WannaCrypt deletes the volume shadow copies, replaces your desktop background image and runs the executable showing the ransom note. During that process, it will also establish persistence by adding itself in the registry as a process to start each time the computer boots up.
The ransomware will demonstrates the decryption capability by allowing the decryption of a few random files. However, remember that nothing guarantees that your files will be decrypted even if you pay the ransom and nothing guarantees you won’t get infected again, especially because of the DoublePulsar backdoor.
The “Kill-Switch”
As part of its process, the malware tries to connect to the following domains:
- iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
If those requests successfully connect to these domains, WannaCrypt stops its execution along with the encryption of your files. While this is currently only an hypothesis, we think that those requests were meant to see if the malware was running within a “Sandbox”, which is a special setup used to analyze malware securely. Stopping its execution makes the analysis harder. Luckily, as part of a standard process during the analysis of the malware, a researcher known as “MalwareTech” registered those domains which had the effect of making the malware think it was always in a “Sandbox”. However, new versions that don’t include the checks have been released.
References:
Microsoft, 15 May 2017, WannaCrypt by Andrea Lelli:
YouTube: How to Disable SMB to Prevent Against WannaCry Attacks:
The Hacker News, 13 May 2017, WannaCry Ransomware Everything you need to know immediately, by Mohit Kumar:
http://thehackernews.com/2017/05/how-to-wannacry-ransomware.html
The update MS17-010:
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4012598
Endgame’s detailed analysis of the ransomware:
https://www.endgame.com/blog/wcrywanacry-ransomware-technical-analysis
Troy Hunt’s analysis of the attack:
https://www.troyhunt.com/everything-you-need-to-know-about-the-wannacrypt-ransomware