
RAC/M Identity
RAC/M Identity™ is a simple, effective, IGA solution that enables organizations large and small to understand and manage the complex relationships between users and their access to physical and digital assets, whether on premises or in the cloud.
It is the cornerstone upon which to build a successful IAM program capable of taming your most daunting challenges such as:
- Lack of resources
- Limited budgets
- Strict timelines
- Complex technological and business landscape
RAC/M Identity™ also addresses one of the most difficult challenges faced by IAM programs – maintaining executive support.
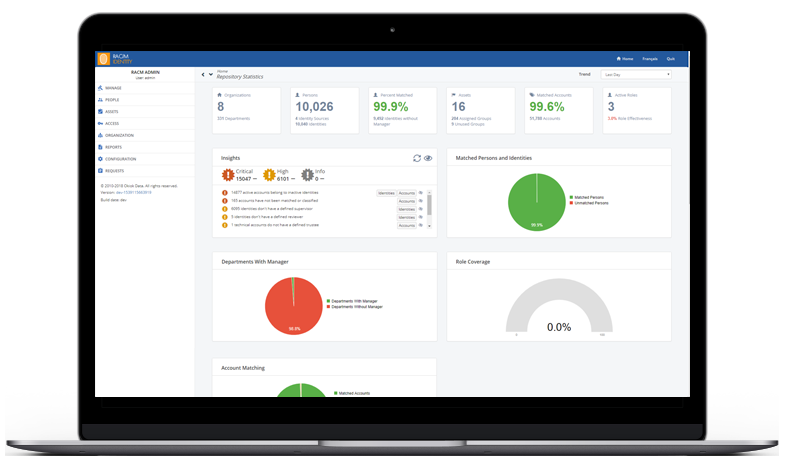
It automatically generates a composite health score that reflects the maturity and effectiveness of key IAM processes, enabling executive management to assess progress made as well as the remaining road ahead on the journey.
See how OKIOK’s clients have used RAC/M Identity as the cornerstone of their IAM strategy.
A DIFFERENT APPROACH, FOCUSING ON IDENTITY GOVERNANCE
RAC/M Identity differs from traditional Identity Governance and Administration (IGA) suites by being part of a full-service offer, backed by a proven, risk free deployment methodology.
Our approach is squarely centered around implementing a solid foundation, focused on enhancing identity governance processes as a prerequisite for automating provisioning.




