Governance
and Compliance
and Compliance
optimal governance
in Cyber Security
Information systems represent over 20% of the annual budget of a company. Thus, it is essential that they are adapted to the company’s context and business objectives.
The current technological context and growing security risks encourage organizations to adopt a structured, responsive and accountable security program.
The “Cyber Security Governance” or “IT Governance” refers to cyber security management tools and security systems regulation mediums that were put in place by a company to achieve its goals.
As such, the security governance is a continuous process being an integral part to the culture of a company, integrating risk management and strategically aligned with its business objectives. It sets the rules of tactical and operational security, such as the establishment of appropriate controls. It provides therefore a compliance with applicable standards and consistency in the implementation of the normative framework.
Whether you are subject to the NIST 800-53, ISO 27000 or PCI DSS (Payment Card Industry Data Security Standard), many companies must comply with specific requirements and adopt best practices in cyber security. Establish policies, guidelines and procedures is the starting point of the governance framework, by developing a comprehensive security program to ensure the appliance of the principles, safety measures and security controls within your business.
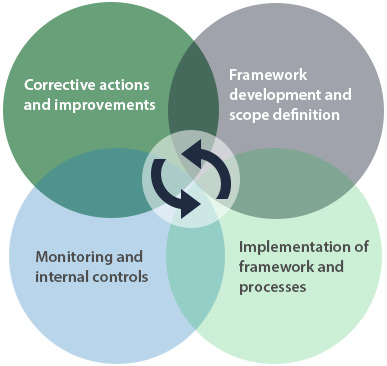
The table below illustrates the PDCA (Plan-Do-Check-Act) method, which allows to establish the foundations of a first ISO / IEC 27001 perimeter and adopt the tools needed to maintain a governance framework.
Our services

Governance

Normative Framework

Audits and assessments

Risk Management

Security Architecture