
Incident response

In case of incident, contact 1-450-681-1681 ext. 277
Information security incidents
Information security incidents are now an integral part of technology environments. They can be accidental (caused by unintentional human error or by unavoidable natural acts) or deliberate (caused by malware or intentional violation of an individual).
The consequences can be catastrophic such as disclosure, modification or destruction of sensitive information, interruption of service, financial losses and reputational damage. At varying levels of severity, incidents require an appropriate response, and their management must be integrated in the overall security strategy of organizations. Depending on the nature of the incident, the incident response will consist of several actions, usually technical, to mitigate the impacts and minimize direct and indirect damage to operations.
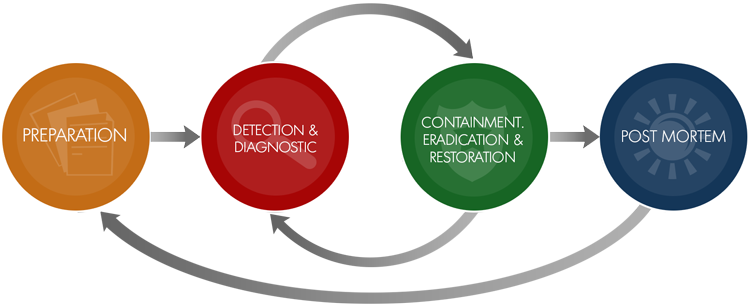
OUR SERVICES
- Establishment of the incident management framework
- Diagnostic and communication
- Containment
- Eradication
- Investigation
- Reverse Engineering
- Recommendations
Case Examples
- Ransomware
- Cyber attacks
- Information leaks
- Web scraping (harvesting)
- Deny of service
- Keyloggers fraud
- Defacement










