
RAC/M Identity™ is our simple and effective identity governance (IAM) solution that enables businesses large and small to understand and manage the complex relationships between users and their access to physical and digital resources, on-premise or in cloud computing.
SIGNIFICANT IMPROVEMENTS
Audit
RAC/M Identity audits have been redesigned to provide much more information about the lifecycle of repository entities.
A new screen displays a list of all audits in the system. This screen allows you to filter the list by audit type and/or by date.
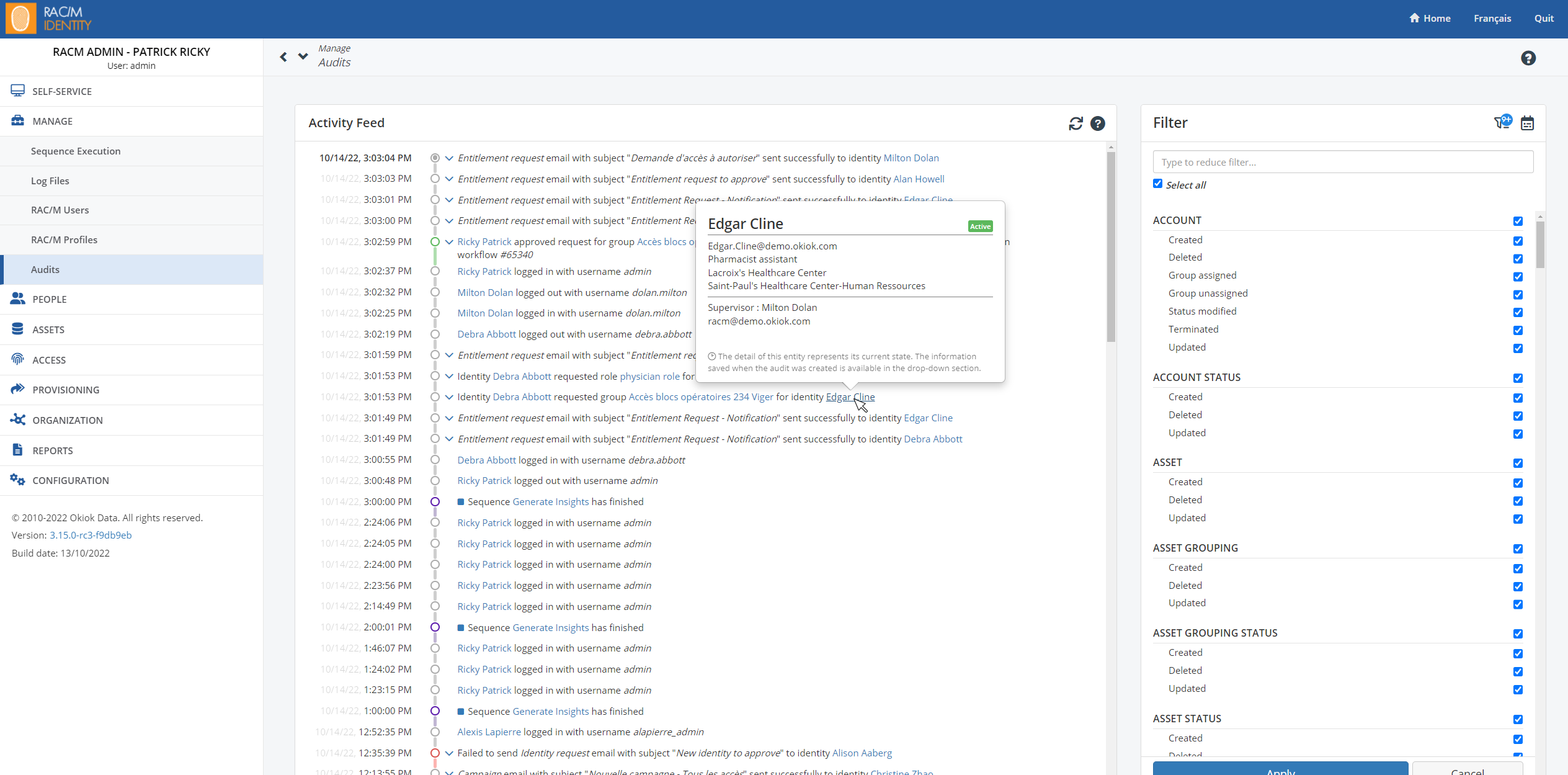
Each audit record is now accompanied by contextual information that allows you to understand the context of the audit when it is written and to follow the life cycle of the entities and requests.
Each entity (identity, account, application, etc.) can now be linked to an audit entry. In the entity details screens, a new “Activity Feed” section allows to see the list of audits directly associated to this entity. This list can also be filtered by event type or by date.
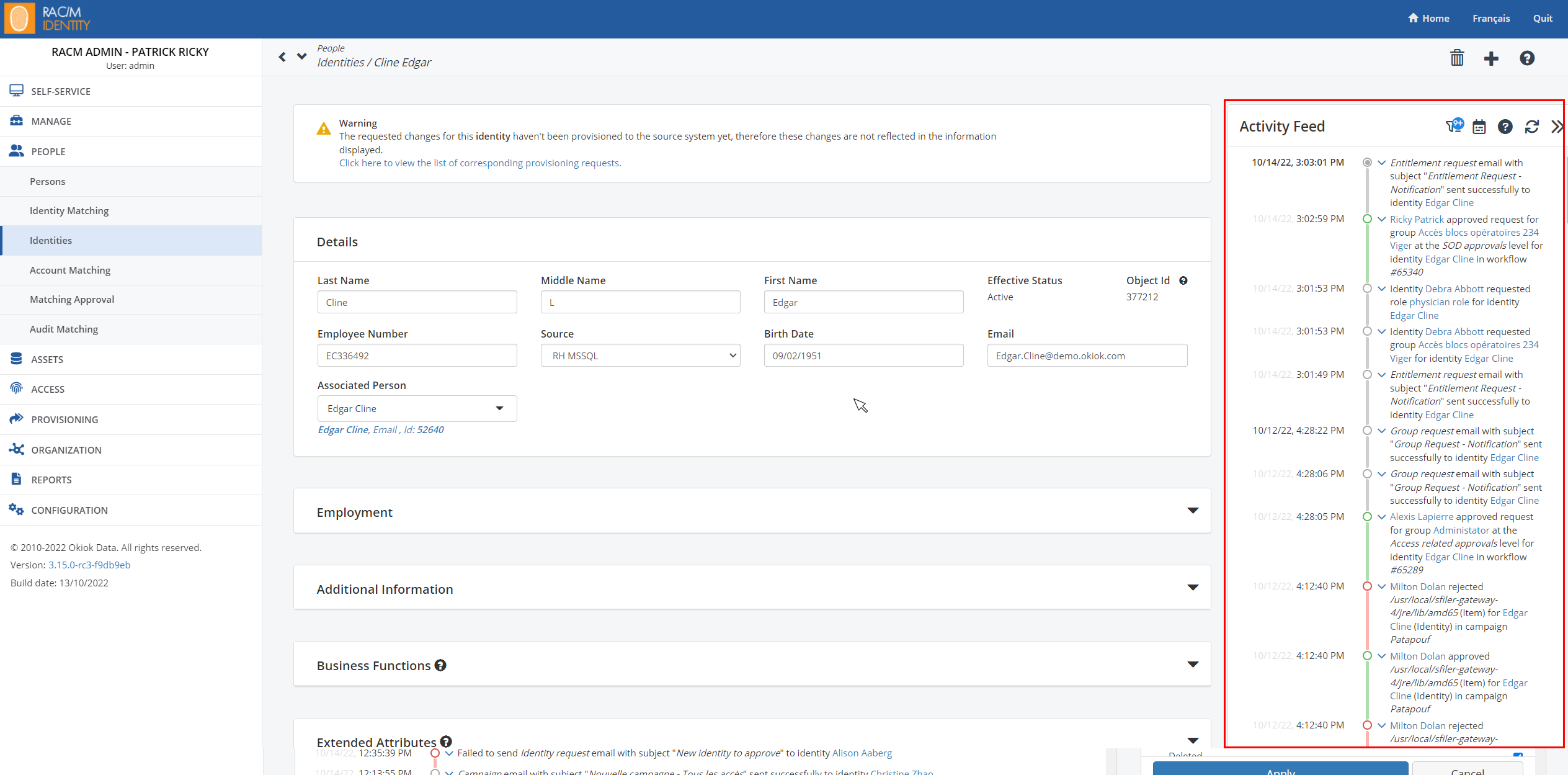
These improvements will have a significant impact on the size of the database used. Clients using the on-premise version of the solution should foresee an increase in the size of the database.
REST API
A new REST web service API has been added to replace the old one based on SOAP technology (the latter remains available, but the new features will be added in the REST API). Here is the list of features (“endpoints”) currently offered:
- Authentication: Allows you to obtain an authentication token for subsequent calls to the API.
- Identities: Allows you to list, search, read, create, save and delete identities, as well as associate or dissociate an identity with a person.
- Persons: Allows you to list, search, read, create, save and delete persons.
- AssetGroupings: Allows you to list, search, read, create, save and delete asset groupings.
- Assets: Allows you to list, search, read, create, save and delete assets.
- Groups: Allows you to list, search, read, create, save and delete groups.
- Accounts: Allows you to list, search, read, create, save and delete accounts. In addition, you can retrieve the groups and identities associated with the account as well as associate or dissociate an account with an identity.
- Workflows: Allows you to make access requests, consultant onboarding, departure notices, etc. This generally corresponds to the requests that can be made in the self-service interface. These requests initiate the appropriate approval workflows and lead to the provisioning of access.
- Provisionings: Allows you to interact with objects related to provisioning. These objects are created as part of the approval flows. The API allows you to re-run requests as well as read and/or cancel individual objects.
The service parameters can be viewed here : https://www.okiok.com/products-documentation/racm-identity/api/v1-experimental/
To view the API documentation on your RAC/M Identity installation, you can simply point your browser to an address consisting of your server host and the relative path to the API documentation ( /api/v1/docs).
For example: https://demo2.racmidentity.com/api/v1/docs/
IMPROVEMENTS
Email Tester
A new screen is now available under Configuration/Email Testers that allows you to batch or unit test the various RAC/M Identity email templates.
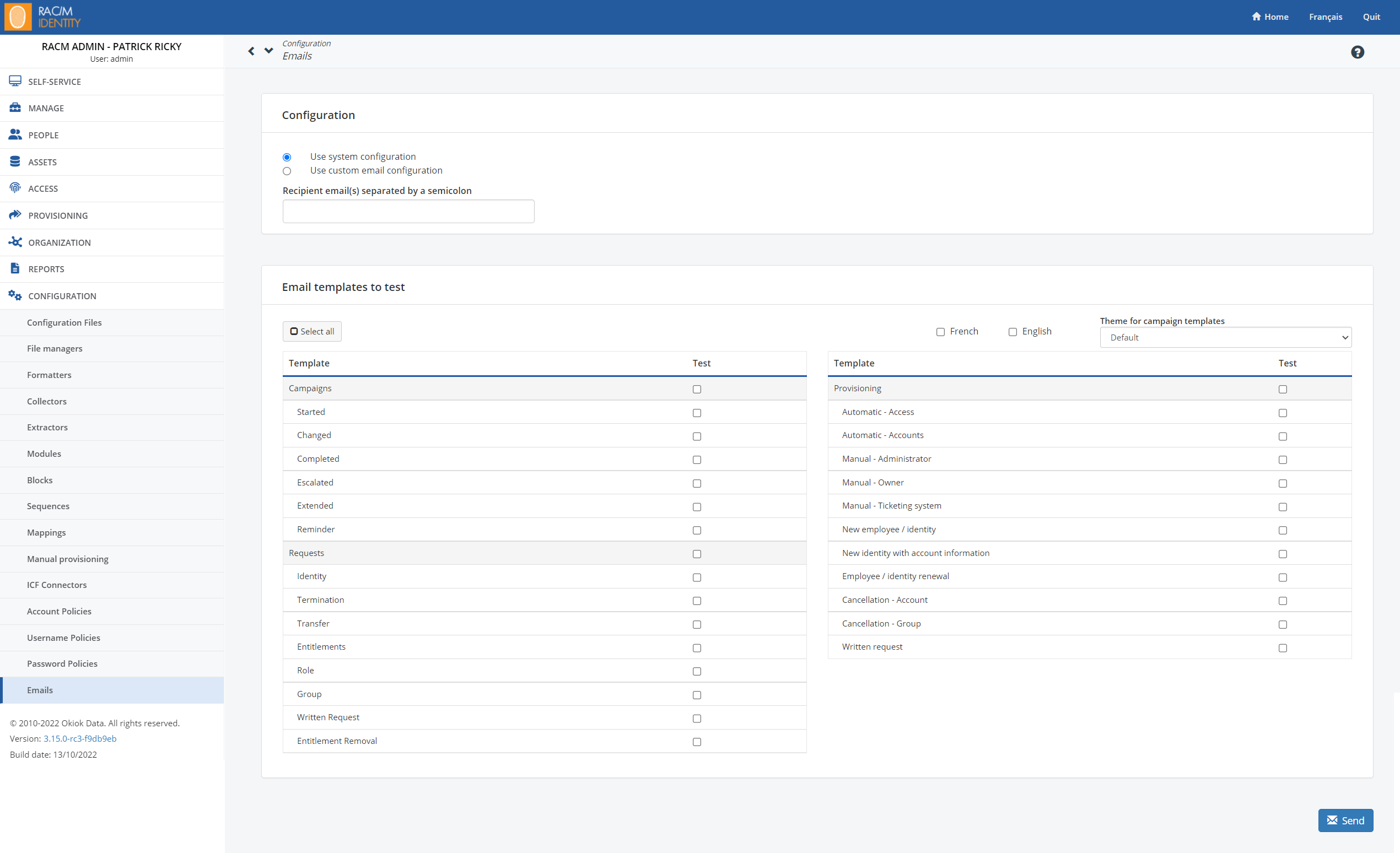
It is possible to run the tests with the email service configured in RAC/M Identity or to use another email server. This allows you to validate the connection parameters of a mail server.
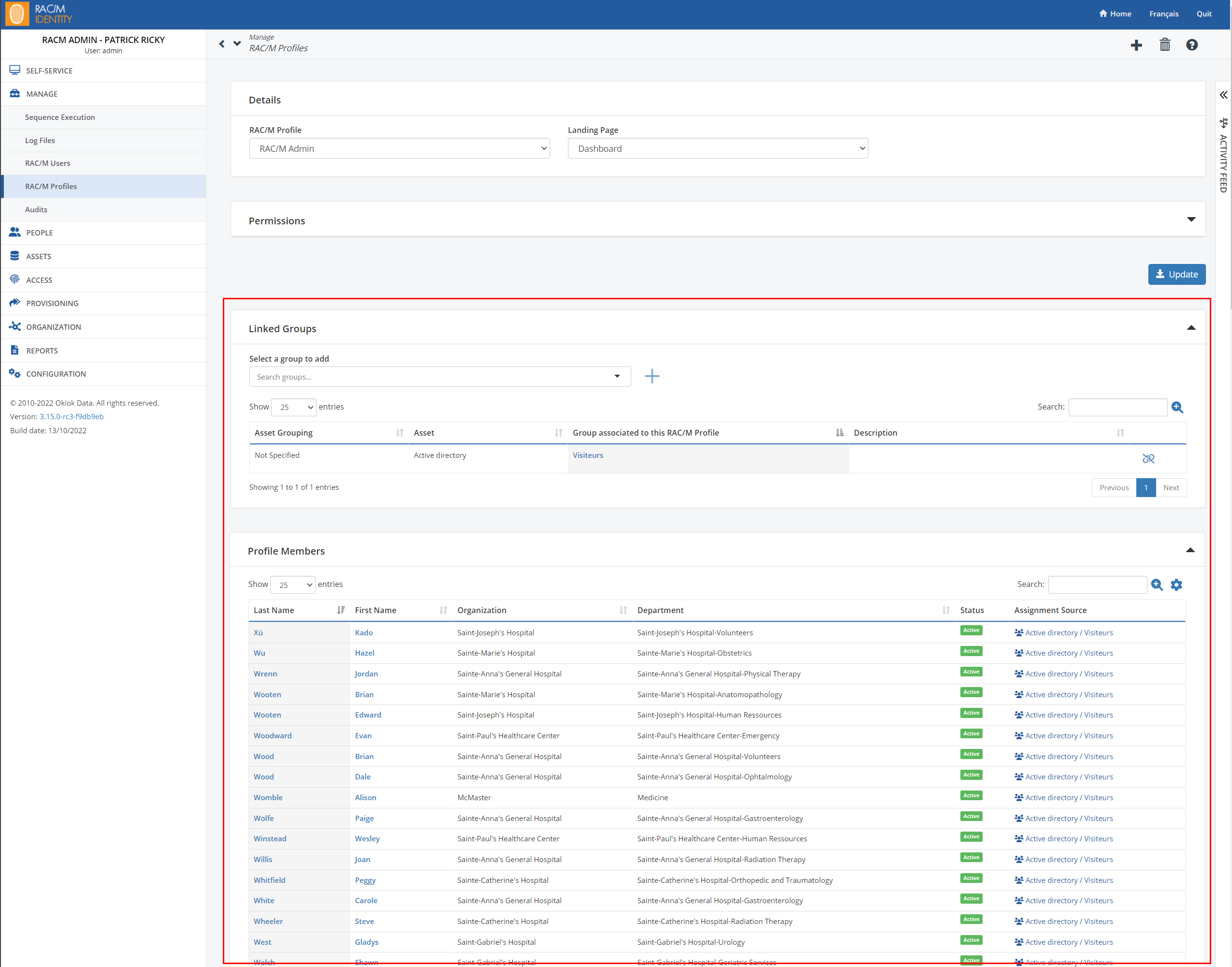
Improved permissions management
RAC/M Identity access profiles can now be associated with security groups of assets managed by the solution (e.g. Active Directory). This simplifies the management of permissions in the solution even if provisioning features are not configured (as is the case for the governance edition). #1006
Warning: Migration to RAC/M Identity 3.15 should be done with care if you are using single sign-on authentications. This requires you to model your Azure Active Directory/Active Directory group relationship with identities in order to maintain access to the user interface.
Self-service
- A few minor changes have been made to the entitlement request screens in the self-service section. #3207 and #3220
- The word ‘Division’ has been changed to ‘Organization’ to be consistent with the rest of the application.
- In the identity search drop-down menus, the department is now visible.
- Dates and times entered in the self-service portal are now displayed according to the user’s time zone.
- In Self Service, when a date was requested to give or remove accesses, it is now possible to specify the precise time when the action should be taken. #3125
- It is now possible to remove the field that asks for the end date of integration of an external identity in the self-service. The following property is available for this purpose in the config.properties file: self.service.new.external.identity.end.date.enable. #3104
Module
- Added modules (ModuleExternalFTPSGet, ModuleExternalFTPSMove, ModuleExternalFTPSMoveArchive and ModuleExternalFTPSPut ) for file transfers with FTPS. #2644
- Added a module (ModuleRunNativeScript) to run scripts native to the operating system (BASH, PowerShell, python, etc.) in a sequence. #2190
- Two new modules have been created to manage the extraction of dates from the permanent code of the Quebec Ministry of Education and the permanent code of the Quebec Health Insurance Board. #3114
- Extended attributes can be used directly in the module configuration. In addition, multi-valued fields from ICF connectors can be associated with extended attributes supporting multiple values. #1394
- It is now possible to select .txt files in collectors. #2225
- The module ModuleExtractSQL has been modified to allow extraction of data from other RAC/M Identity databases (config, workflow). #317
Other
- The LAST_SYNC_DATE column has been added for reconciliation management. Previously, RAC/M Identity used the LAST_MODIFIED_DATE column which caused processing errors when the item was manually saved in the UI during a sequence run. #2938
- The report list has been enhanced to provide better filtering capabilities. #2806
- The list of review campaigns that can be selected when launching an incremental campaign has been improved. #2809
- Added description column in the list of account provisioning. #3158
- Start and end dates have been added to the list of identities. #2973
- Changes have been made to the server to allow extended attributes to be displayed in the email template ‘AutomaticProvisioning_account.html’. #2963
BUG FIXES
Module
- In the ModuleCorrelationByDomainAccountName module a correlation error was fixed when the match field had a ‘%’. #3097
- A copy error in the ModuleCopyColumnsAndInsertSQL module has been fixed when the SUPERVISOR_ID is set in the module’s data copy configurations. #3121
- Correction of the selection of the account policy strategy during the manual provisioning in module ‘ModuleManualProvisioningRequest’. #3205
- The ModuleDeleteNonUpdatedSinceDate module no longer processes accounts that already have the status “TERMINATED” when configured to “terminate” accounts without deleting them. #2683
Review Campaign
- Corrections to the transfer function of the review campaign. In several successive transfer requests, some transfers did not work, but the interface indicated otherwise. #3165
- In a review campaign, if an identity was rejected, the interface required the user to enter a comment, but the “Yes (reject)” button was usable and allowed the request to be submitted without comment. This has been corrected.
- When a campaign is saved in preview mode, the notification dates are calculated. When the campaign was started, these dates were not recalculated. This has been corrected to recalculate the notification dates when the campaign is started. #3167
- Corrections to the display of SOD rules in the review campaign screens. #3226
- Completed reviewers are no longer assigned a review. Reviews are transferred to the review campaign manager. #3139
- Fixed a problem with the generation of campaigns by account trustees when the account has several groups. #2997
- The “Approve All” feature has been fixed when the review campaign is filtered by group. #275
Other
- A clarification has been made to the role version screen to better distinguish between the role description and the version description. #2877
- Approving a request now cancels redundant tasks and requests for the same entitlements. #2762
- When activating a new version of a given role, RAC/M Identity would attempt to cancel all pending requests for that role. This has been fixed. #3132
- When starting the server, the call to the terracota.org service to check if the ehcache library should be updated was disabled.#3103
- The lists of miscellaneous items in the user interface have been corrected to allow the use of special characters in the filter field such as ‘+’ and ‘%’. #3178
- The identities page has been corrected so that it no longer fails when one of the identities in the list is associated with a supervisor that no longer exists.#3022
- When duplicating the dynamic roles, the inclusion criteria were not duplicated. The criteria are now copied. #3087
- In some cases, it was possible for manual provisioning requests to be processed twice. This situation has been corrected. #3099
- To reduce the possibility of identity theft, a user can no longer pair their accounts with other identities or pair other accounts with their identity. #2967
- Corrections to the saving of an asset. The Identifier1 and Identifier2 fields are now saved normally.#550
- It is no longer possible for a user to cancel their own request once it has been fully approved. This fixes a vulnerability where a user could cancel the access removal request in the future once accesses had been granted with an end date. #3171
- Fixed unexpected account closure during provisioning. This was happening when an AccountManagement contained only one AccountManagementProfile and it was for a group that was already deleted.#3187
- Corrections to the permissions management in the “Tasks” screen in relation to a RAC/M Identity user profile. #3146
- Some changes have been made to the account matching screen to reduce the level of confusion with matching accounts with trustees. #2116
- When a transfer is auto-approved (done by the identity supervisor), there was no task created and the identity changes remained in the “PENDING” state. A self-approved task is now created and the identity changes are changed to the “APPROVED” state. #3090
- Corrections to date formats in the provisioning screens. #3227
- When deleting a group, the associated tasks and requests are now cancelled correctly. #2924
- Transfer requests via the self-service could result in the withdrawal of some entitlements given by dynamic roles. This has been corrected. #2949
- Some group requests were not associated with a RAC/M Identity workflow. If these requests were redundant, they were not cancelled when access was granted. This has been corrected.#3188
- A refresh error in the sequence description has been corrected in the sequence execution screen. #2974
- In some situations, contractor renewal tasks were not processed correctly when cancelled and this caused the renewal module to fail to run afterwards. This issue has been fixed. #2980
- Fixed the workflow engine that could be in an unrecoverable state. This behavior forced the server to be restarted. #3246
- General fix to the worflow engine to prevent some rare situations where the engine would end up in a corrupted state and fail on every workflow related action and needed a server restart to correct. #3246
BREAKING CHANGES
These new properties must be added to the config.properties file of current RAC/M Identity installations
- Source system multi-value import
- When importing multi-values fields from a source systems, such as Microsoft Active Directory, multi-values that are mapped to single values in RAC/M Identity will cause the sequence to fail. These multi-values must be mapped to multi-value extended attributes.
- Dates
- self.service.new.external.identity.end.date.enabled=true
- Displays the end date field in the self-service for the integration request of an external contractor.
- self.service.future.request.min.date.override=
- The number of minutes in the future to apply on date selectors that request a date in the future. If one of these dates is submitted in a request and it is in the past, the request fails because of that date. The purpose of this value is for the user to submit the request with a date far enough in the future that when it is submitted and processed by the server, the date will not be in the past. The default value is 15, so that the selected dates are 15 minutes in the future.
- self.service.new.external.identity.end.date.enabled=true
- Keystore to define the keys used for OAuth 2.0 authentication used by the REST API
- This keystore which is configured via the `webserver.api.keystore.*` configurations is used to sign the OAUTH2.0 token for the REST API.
It is recommended to generate a new key pair and not to use the same certificate as the RAC/M user interface certificate. - The following configurations are used to access the certificate during OAUTH authentication:
- webserver.api.keystore=[PATH THE KEYSTORE FILE]
- webserver.api.keystore.password=[KEYSTORE PASSWORD]
- webserver.api.keystore.private.key.alias=[ALIAS OF THE PRIVATE KEY]
- webserver.api.keystore.private.key.password=[PRIVATE KEY PASSWORD]
- webserver.api.token.expires_in_seconds=[NUMBER OF SECONDS BEFORE THE TOKEN EXPIRES]
- Authentication token expiration time. This number is in seconds.
- This keystore which is configured via the `webserver.api.keystore.*` configurations is used to sign the OAUTH2.0 token for the REST API.
- Campaign
- incremental_campaign_list.size
- The list of possible sizes for the incremental campaign list. The default value is 5,10,25,50.
- incremental_campaign_list.size
- Audits
- number_fetched_audits
- The number of items retrieved from the audit page. The default value is 100. The maximum is 4096.
- number_fetched_audits




