
RAC/M Identity™ is our simple and effective identity governance (IAM) solution that enables businesses large and small to understand and manage the complex relationships between users and their access to physical and digital resources, offered as an on-premise or SaaS solution.
NEW AND NOTEWORTHY
Review Campaign – Reviewer Group
The assets and groups have been modified to allow the configuration of a “Reviewer Group”. This will be used in review campaigns where elements need to be reviewed by someone linked to the asset. Previously, these review campaigns assigned the review to the asset owner but this gives more flexibility as the reviewer can be the same as the owner or different. #3004
In the assets:
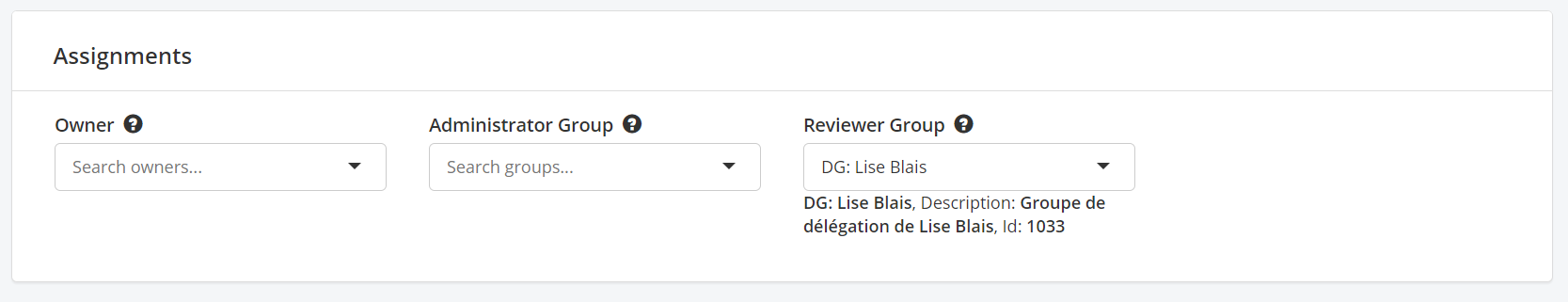
In the groups:
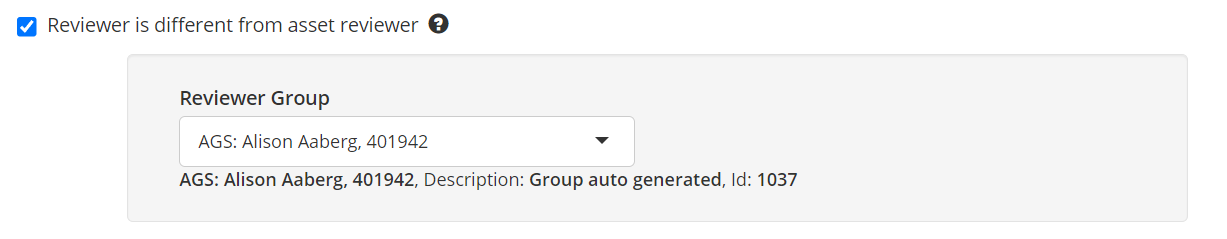
* When the system starts after the update, delegation groups will be created automatically with the current asset owners and set in the “Asset reviewer” field so that the current behavior in campaigns remains unchanged.
When a reviewer is defined on a group, it overrides the configuration of the reviewer on the asset. #3117
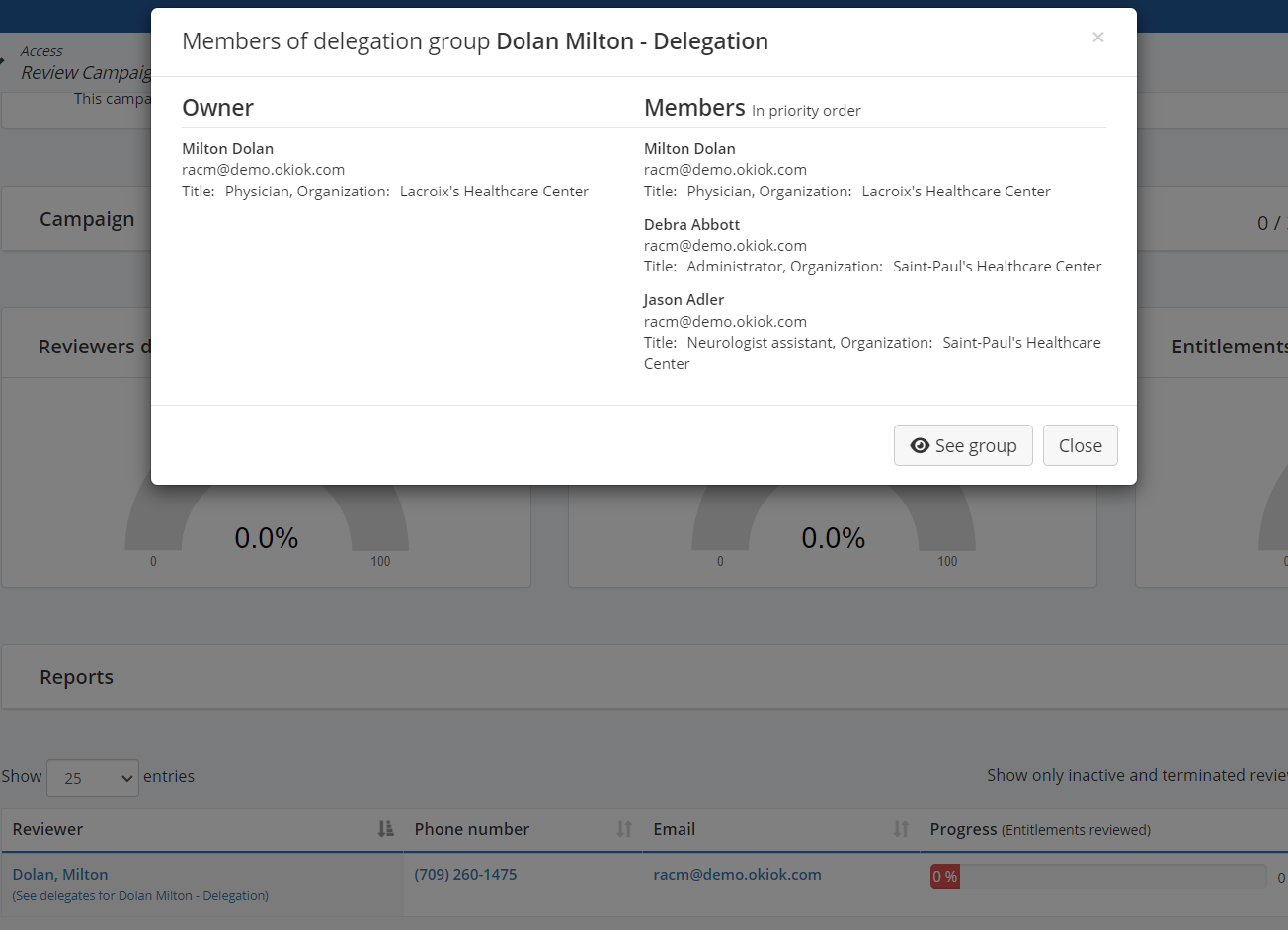
In the campaign management screen, a link “(See delegates from [delegation group name])” has been added under each reviewer to display the list of delegates for that reviewer in this campaign.
Review Campaign – Filter
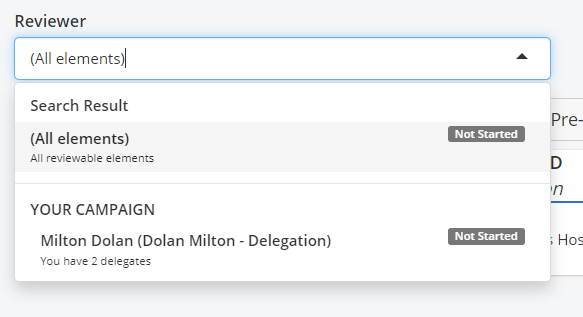
In a given campaign, a reviewer can be part of multiple delegation groups each having some elements to review in the campaign. These elements are properly segregated so that only the members of a delegation group can review the elements assigned to it. The solution now provides visibility to the reviewer of these different delegation groups that he is a part of and allows filtering the elements to review based on them. The default filter is to see all elements from all delegation groups which was the behavior before this feature was introduced. #3377
Review Campaign – Asset reviewer
A new option was added to have “Asset reviewers” review the elements in campaigns of type “All entitlements” and “Identity review – Only show accounts (entitlements of those accounts are not shown)”. This uses the new “Asset reviewer” functionality mentioned above. Previously, only “Identity reviewers” or “Specific reviewer” could be used in these types of campaigns. #3117
Review campaign – Role content reviewer (groups, included roles and access)
A new option was added to determine who should review the elements in campaigns of type “Role content review – Included roles and entitlements”. This option “Role content reviewers (groups, included roles and accesses)” selects the reviewers based on the content of the role (security groups or nested roles) to review whether these accesses should be given when the role is assigned to an identity. Previously the only option available was to have the reviewer of the parent role review which entitlements should be part of his role. #2631
Text editor
It is now possible to create, edit and delete configuration files and data files in the administrative console. It is also possible to delete log files in this console. #1870
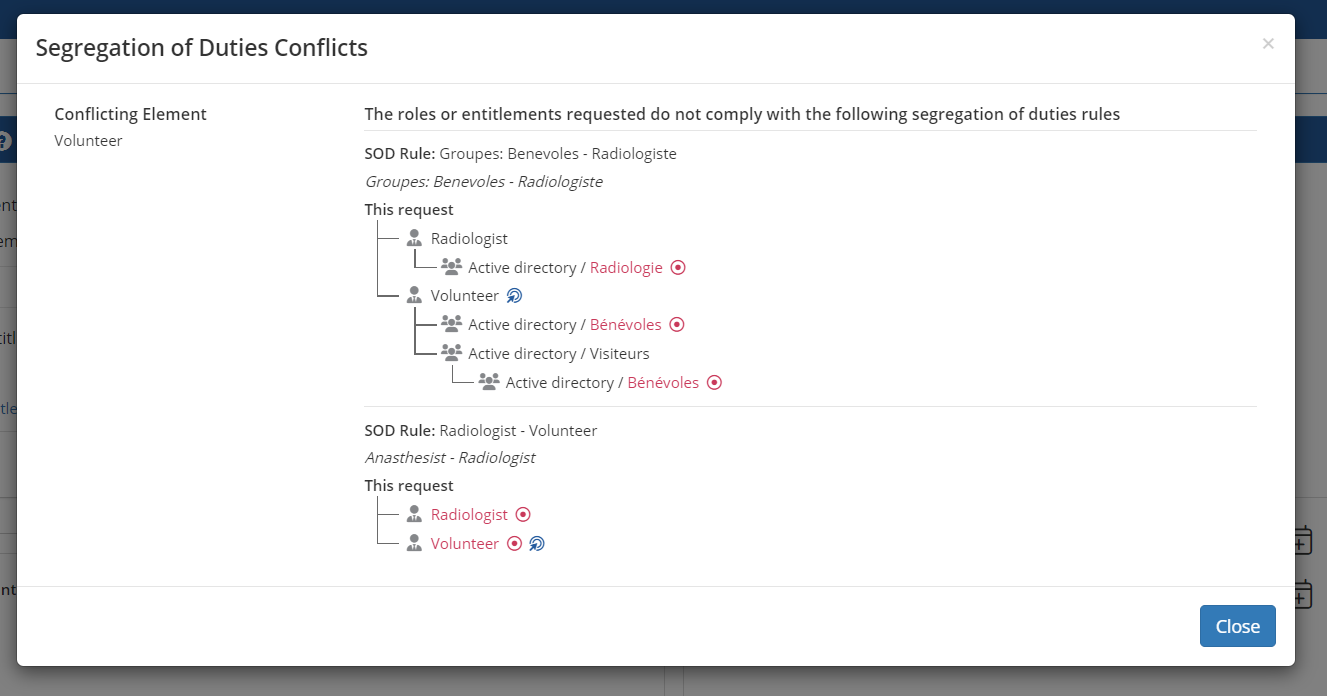
Segregation conflict
In the Self Service portal, when a user requests accesses that results in an SOD conflict, there is now a detailed screen showing the exact reason for the conflict including any intermediate entitlement. #2987
IMPROVEMENTS
- When deactivating a role, a confirmation window is now displayed before proceeding with the deactivation. #3115
- Several improvements to the Microsoft 365 connector
- Accept additional attributes associated with users: city, companyName, country, createdDateTime, creationType, deletedDateTime, employeeHireDate, employeeId, employeeType, externalUserState, externalUserStateChangeDateTime, faxNumber, imAddresses, isResourceAccount, lastPasswordChangeDateTime, mailNickname, onPremisesDistinguishedName, onPremisesDomainName, onPremisesImmutableId, onPremisesLastSyncDateTime, onPremisesSamAccountName, onPremisesSecurityIdentifier, onPremisesSyncEnabled, onPremisesUserPrincipalName, otherMails, passwordPolicies, postalCode, preferredDataLocation, proxyAddresses, refreshTokensValidFromDateTime, signInSessionsValidFromDateTime, state, streetAddress, usageLocation and photo. #1709
- Accepts attributes associated with TEAMS groups joined by users. The following attributes are now used by the connector: users.id, user.displayName, team.id, team.createdDateTime, team.displayName, team.description, team.internalId, team.classification, team.webUrl and team.isArchived. #3347
- Reads the owners of Azure AD groups linked to Sharepoint. The following attributes are now used by the connector: id, displayName, description, owner.id and owner.type. #3297
- The Active Directory connector has been modified to support deletion of attribute content during provisioning. #2202
- Improved handling of the CSRF security token. In line with best practices, when performing HTML GET operations, the token is no longer required. This will eliminate issues that occurred when multiple browser tabs / windows were opened and the session expired. In addition, it will allow pages to be bookmarked and returned to directly in the future without being redirected to an error page. Finally, the filters of all lists are saved in the URL and can be bookmarked. #3217
- It is now possible to delete all criteria in a dynamic role which has the result of assigning the role to everyone. (The role can be converted to a static role if it needs to be assigned only to specific identities). #1258
- Added/improved descriptions in a large number of modules, collectors and formatters. #3389
- Added granular control over notifications when provisioning accounts and groups. New sections have been added in assets and groups to configure whether a notification should be sent when provisioning them. #3314
- On first startup following the upgrade, these new configurations will be migrated from the following two configuration items in the config.properties file:
- Groups: mail.request.automatic.provisioning.profile.notification
- Accounts: mail.request.automatic.provisioning.account.notification
BUG FIXES
- In ModuleCorrelationByDomainAccountName a correlation error was fixed when the match field had a ‘%’. #3097
- Corrections to the authorization rules of some pages to align them with the correct authorization model. #3334 and #3344
- A fix has been introduced to eliminate a session error when reviews are performed over a long period of time in review campaigns. #3127
- The order in which approvers are displayed in tasks has been changed to reflect the priority order established in the delegation groups. #3302.
- The content review report in a role review campaign could cause a service interruption due to excessive memory usage. A fix has been made to eliminate this issue. #3336
- Some conditions could allow the presence of more than one sequence with the same name. This made it impossible to execute these sequences. A fix has been added to not allow two sequences with the same name. #2889
- Fixed email notifications to always use the language of the recipient. In some cases, the message was not sent in the user’s language but in the language configured for the system. #3265
- Fixed the save button at the top of the campaigns page. This button caused an error when a campaign was duplicated. #3305
- When an underscore was used in an extended attribute, an error occurred when the same value was used in another instance of the same attribute type. This problem has been resolved. #3152
- Fixed a problem that caused some reports to crash due to excessive memory use. The issue was related to the image cache. #3338
- Improved performance when a group is deleted. #3355
- Fixed the display of the supervisor of a reviewed identity in review campaigns. In some cases, the reviewer was displayed instead of the supervisor. #3224
- Fixed the template for the start of a review campaign email. The variable that displays the start date, @{displayCampaign.campaignStartDate}, is now available. #3046
- Fixed an issue where, in rare circumstances, assigning a role to an identity would provision entitlements to other identities that were members of inactive versions of roles that included the assigned role. #3044
- Fixed the import of extended attributes of boolean type. #3350
- MODULES
- Fixed ModuleCopyCSVToTable module when importing an XLSX file without column headers. #3394.
- Fixed ModuleHRTerminationDate module processing identity termination dates multiple times for the same identities when dates are added manually with SQL queries. #3300
- Fixed ModuleCreateLogicalObjectsWithRegex, the field “Replaces the target asset at which logical elements will be created” is handled correctly now when updating logical group. #3372.
- Improved ModuleCopyColumnsAndInsertSQL module, it now supports comparing values in a case sensitive way depending on configuration. #3225
- Fixed an issue where a formatter configured for a file with an empty column name could not reload and display its configuration after it was saved. #3393
BREAKING CHANGES
Duplicate configuration property
Changed the behavior of the server to detect the configuration error when the same value is present more than once in the configuration file. In these cases, the server will not start and will indicate the error instead of starting and taking one of the duplicate values at random. #3313
If you have duplicate configuration properties in the config.properties file, a startup error will occur. For example, if you set the webapp.theme property more than once, you will see the following message in the RAC/M Identity server log during startup:
One or more duplicate keys are present in conf/config.properties for: webapp.theme
To avoid this error, make sure that each property in the config.properties file is set only once.










