
S-Filer Portal™ is a complete solution that enables large and small organizations to meet all of their enterprise needs for secure file transfer and storage.
OKIOK RELEASES VERSION 4.17.0 OF S-FILER/PORTAL™ SECURE TRANSFER SOLUTION
New and Noteworthy
This version introduces new features to the solution.
Greater flexibility for Shares
Shares are intended to make it easier to share files with external users. The new version of the feature adds more flexibility.
- It is now possible to send invitations by specifying the name, language and role of the user in the Share.
- It is also possible to transfer the ownership of a Share to another user than its creator.
- REMINDER: The Share feature is not enabled by default in the application.
The process of creating a Share is done in two steps:
The first step is only to give the Share a name and a potential expiration date.
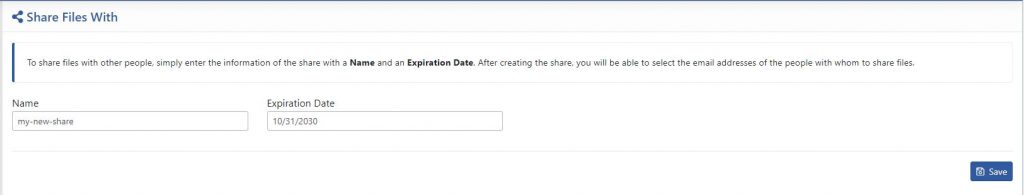
The second step is where the user invitation process takes place. You must begin the process by entering the email addresses of the invited users or the names of users already in the user base. Once these are selected, after pressing “Add”, a modal window will be proposed and will allow you to select the characteristics of the members of the Share. You will be able to write a personalized message to the users who will receive an email inviting them to connect.
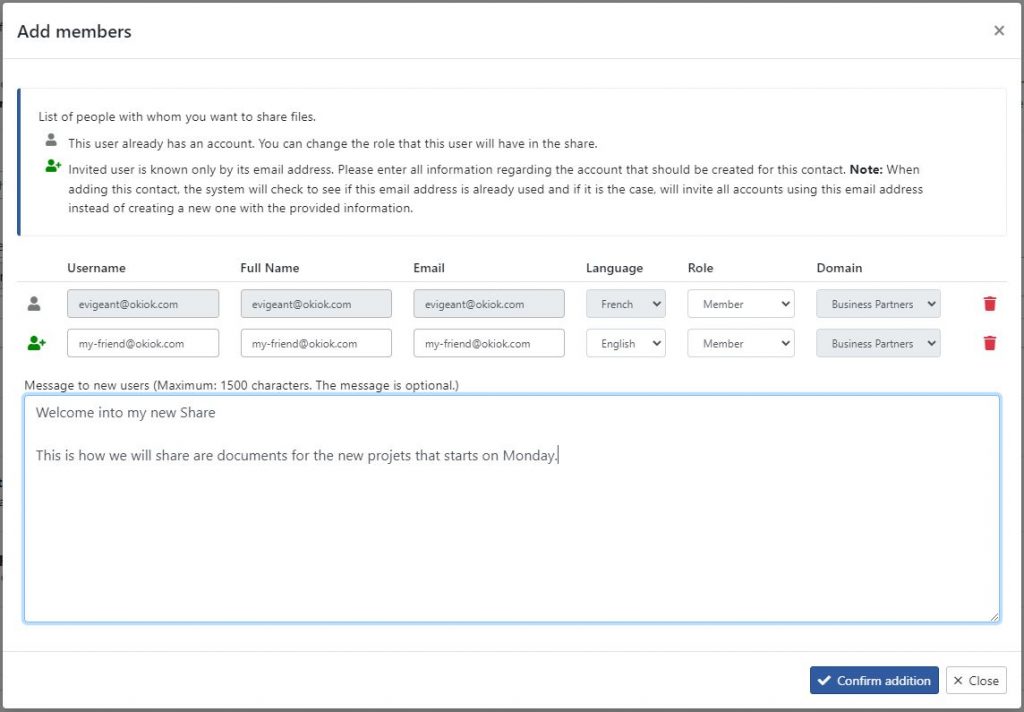
Once the invitation is complete, you will return to the Share configuration screen. You will be able to issue new invitations as needed and remove users who should no longer be in the share space.
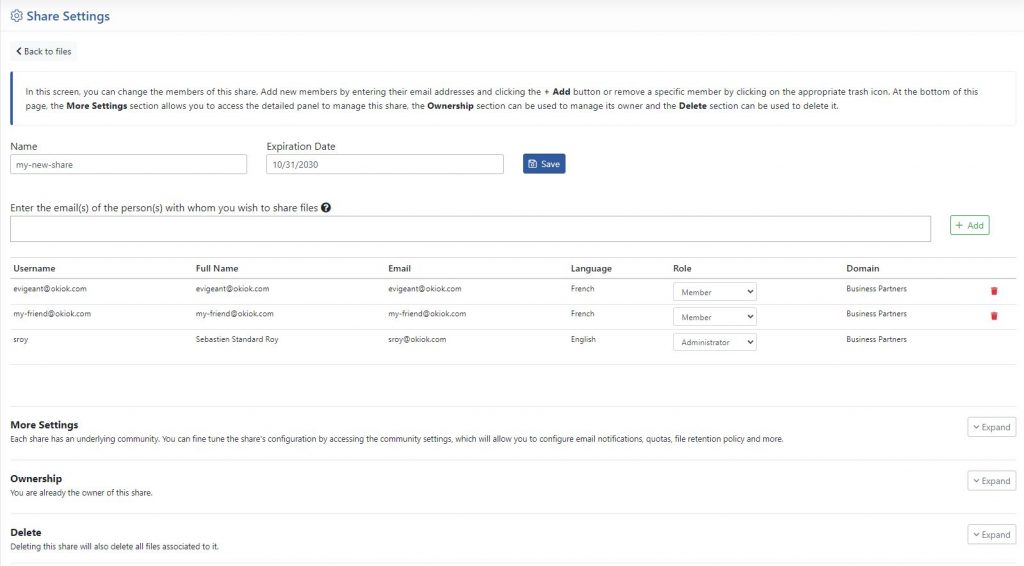
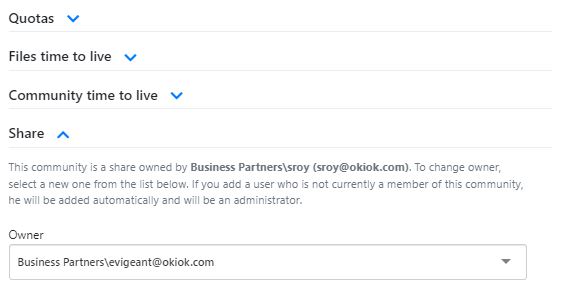
It is also now possible to transfer ownership of a Share to another user. There are two possible ways to do this:
First, an administrator of the Share can take the initiative to become the owner of the Share. The previous owner will remain an administrator of the community associated with the Share, but will no longer be the owner.
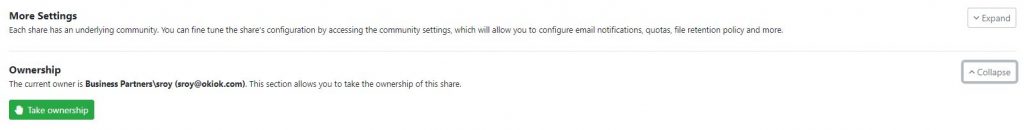
Second, a system administrator, through the community management screens, can assign the share to another user. By doing so, the new owner of the share space will automatically become an administrator of it.
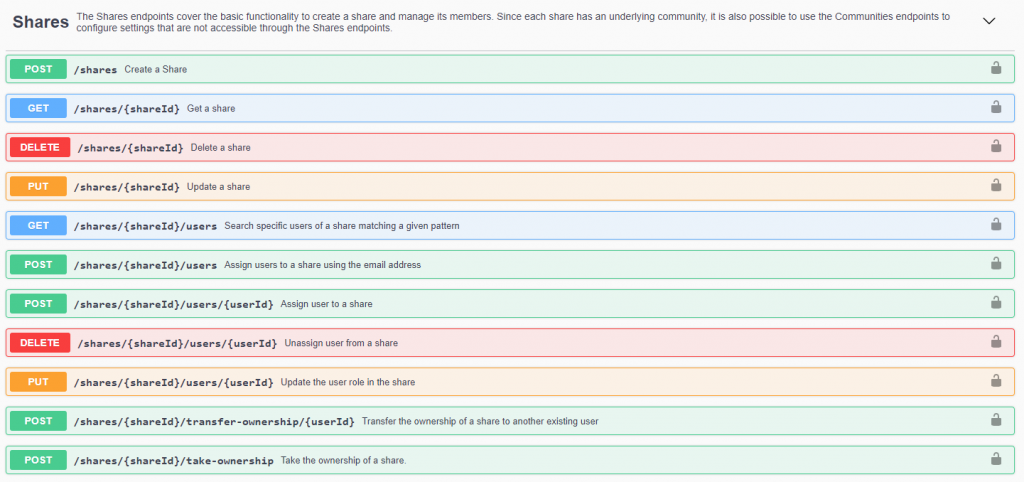
Availability of a REST API for Share management
A new REST API dedicated to Shares is now available. You can view it using the API documentation web page on your S-Filer Portal server. To get it, just open your browser and use the following url: https://SERVER_URL:8088/api/docs/ (replace SERVER_URL with the address of your server and check that the protocol and port are correct for your environment).
More flexibility in configuring encryption algorithms for different protocols
It is now possible to be much more precise when configuring TLS for different file exchange protocols. During a secure connection, the client and the server negotiate which encryption algorithm they will use from the lists of algorithms supported by each of them. The server begins the exchange by sending the list of algorithms it supports and then the client chooses which algorithm to use from that list. Normally, a client always chooses the most secure one from the common algorithms between those it supports and those the server supports. The following configurations change the list of algorithms supported by the server.
For HTTPS and FTPS, the three modes of operation are
1. JVM Default, the server supports all encryption algorithms enabled in the JVM.
2. Automatic, OKIOK determines the list of the most secure encryption algorithms and does not allow the use of encryption algorithms that are considered weak or have known vulnerabilities or attacks.
3. Custom, the client can determine the exact list of encryption algorithms to allow.
Here is a link that describes the encryption algorithms supported by the JVM (see the SunJSSE Cipher Suites section):
https://docs.oracle.com/en/java/javase/18/security/oracle-providers.html
For SFTP, the three modes of operation are as follows:
1. Allow Weak, the server supports all encryption algorithms enabled in the JVM.
2. Automatic, OKIOK determines the list of encryption algorithms considered the most secure and the server only allows these.
3. Custom, le client détermine la liste des algorithmes de chiffrement à utiliser.
Voici un lien qui décrit les algorithmes supportés par la librairie SFTP (voir la section Ciphers):
https://jadaptive.com/app/manpage/en/article/199483
Added new settings for SFTP protocol
There were some environment variables that allowed you to change the default behavior of the SFTP server. If you were using these environment variables, you must now configure them in the administrative console. These are the following variables:
1. “Maximum concurrent transfers” which was previously associated with the environment variable : sfiler.sftp.max.concurrent.transfers
2. “Permanent transfer threads” which was previously associated with the environment variable : SSHD_PERMANENT_TRANSFER_THREADS
3. “Idle timeout” which was previously associated with the environment variable : SSHD_IDLE_CONNEXION_TIMEOUT_SECONDS
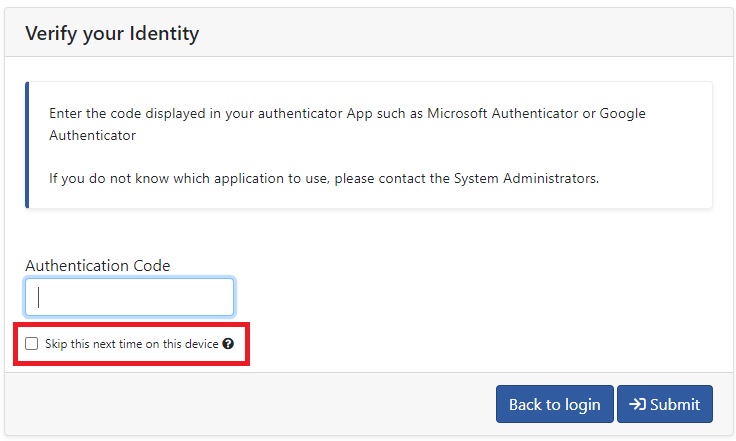
Skip MFA step on trusted devices
When performing an MFA authentication on a trusted device, the user can select to mark this device as trusted to skip the MFA authentication on this device. When this option is selected, the system generates a long-lived token to store on the device which is sent along with the authentication information. With this token, the user does not have to enter the second factor while authenticating.
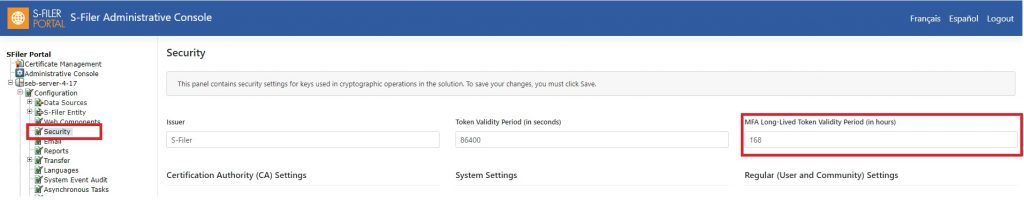
The duration of the long-lived token can be set in the configuration interface on the “Security” page under “Server”:
Minor improvements and bug fixes
- It is now possible to view roles in the user list.
- The date validation process in the report screens has been reviewed and corrected.
- The quota validation process in the communities screen has been reviewed and corrected.
- A new validation has been added to ensure that it is not possible to delete a user who owns a share space.
- A fix has been made to allow uploading a directory using the web interface (“drag-and-drop”).
- A fix has been made to stop sending email notifications to an inactive user.
- The error handling in the administrative console has been reviewed and corrected to give better feedback to the user when an error occurs.
- The “Start Now” button in the various tasks of the Administrative Console Scheduler has been corrected so that it can be used more than once without having to leave the screen.
- The SSL Certificate Management screens have been revised to avoid deleting certificates or key pairs that are in use. The server certificate that was automatically added in the list of trusted certificates has been removed from the list to avoid deleting it by mistake.
- A fix has been made to the list-domains command of the sfiler-admin-cli to avoid an error message when displaying the result.
- The rsa1024-sha1 key exchange algorithm that was considered strong is now considered weak.
API and compatibility changes
- A return code 206 is now returned at authentication time if the user’s password has expired.
Known issues
- Normally, if SSL is enabled, S-Filer Portal will attempt to use TLS 1.3 (unless you use Custom mode and exclude 1.3 Ciphers). However, using TLS 1.3 in FTPS can potentially cause problems with some clients when the SSL/TLS encryption handling mode is set to the “JVM Default” option. It is recommended to leave the value “Automatic” in order to exclude the TLS 1.3 encryption algorithms. It is also recommended not to include the TLS 1.3 encryption algorithms TLS_AES_128_GCM_SHA256, TLS_AES_256_GCM_SHA384 and TLS_CHACHA20_POLY1305_SHA256 when the “Custom” mode is used. This issue will be fixed in version 4.18.0 when upgrading to version 17 of the JVM.
Breaking changes
- The applet has been removed from the solution. It is recommended to migrate to the end-to-end encryption technology introduced in the solution and available with modern browsers.
- The behavior of the REST API has been modified so that the 200 return code, often used to signify the success of a call, no longer returns any message in the response.
- The “Password Policy” web service will soon be removed from the solution and replaced by a REST service from our regular API. All the functionality offered will be replicated through the new REST service.
Update
This version introduces a change to the database model and requires the use of sfiler-config-cli to complete the upgrade. We strongly recommend that you perform a full backup of the solution before upgrading. Do not hesitate to contact our support group if you have any questions regarding this upgrade. support@okiok.com










