
RAC/M Identity™ is our simple and effective identity governance (IAM) solution that enables businesses large and small to understand and manage the complex relationships between users and their access to physical and digital resources, offered as an on-premise or SaaS solution.
MAJOR IMPROVEMENTS
Account status management (#3674).
RAC/M Identity now handles account deactivation more efficiently in identity activation, deactivation and termination flows.
- An active identity can be terminated or deactivated.
- An inactive identity can be reactivated.
- A terminated identity cannot change state: it will remain terminated.
RAC/M Identity is now able to detect changes in account status in the HR source. The appropriate status is therefore correctly assigned to the identities associated with the accounts we receive. This improvement optimizes account status management. This logic is achieved via the “Source employment status” field that has been added to identities. The value of this field can only be modified through provisioning and cannot be modified in the user interface. In the event of a modification to the effective identity status, identity status modification requests are also created.
In order to handle these requests, a new module, “ModuleProcessStatusModificationIdentityManagements”, has been created. This module is responsible for activating, deactivating and terminating identities linked to identity requests, enabling easier management of status modifications. In particular, it is responsible for creating corresponding requests such as account termination requests.
Furthermore, inactive identities no longer receive e-mail notifications. This measure is designed to avoid sending unnecessary notifications and to focus our communications on active identities.
For more details, see the documentation.
Provisioning without target system reconciliation (#1525)
Depending on the RAC/M Identity operating mode, a manual provisioning request can now be triggered according to the mechanism selected.
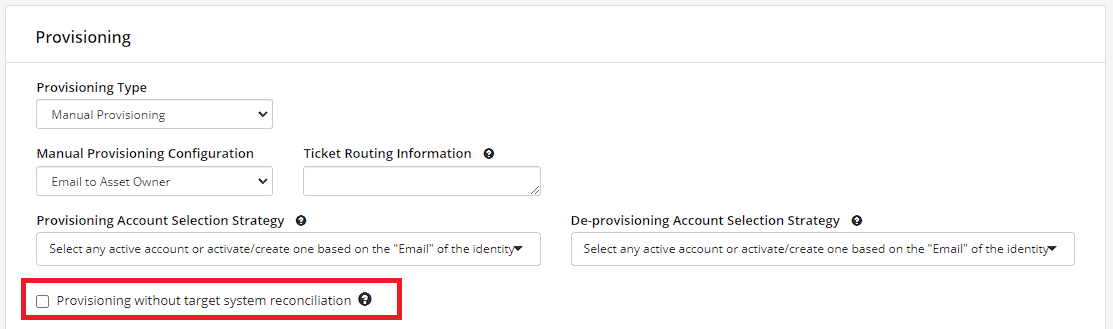
Asset – Provisioning without target system reconciliation
When this option is checked, the application takes into account the fact that there is no reconciliation with the target system. Consequently, all changes are immediately reflected in the repository after the request has been sent.
However, please note that in the absence of reconciliation, there may be significant discrepancies between the repository and the target system. It is therefore essential to understand that data accuracy depends largely on the frequency of reconciliations. This mode is generally used for assets that are reconciled infrequently.
ADDED NOTIFICATION GROUPS (#3630)
A new option has been added for sending notifications to a group of people who are part of the same notification group.
Notification groups work in a similar way to delegation groups. They are available in the identity, asset grouping, asset and group screens.
- In the identity screen, the field is located in the “Employment” section, under “Group to be notified during provisioning”.
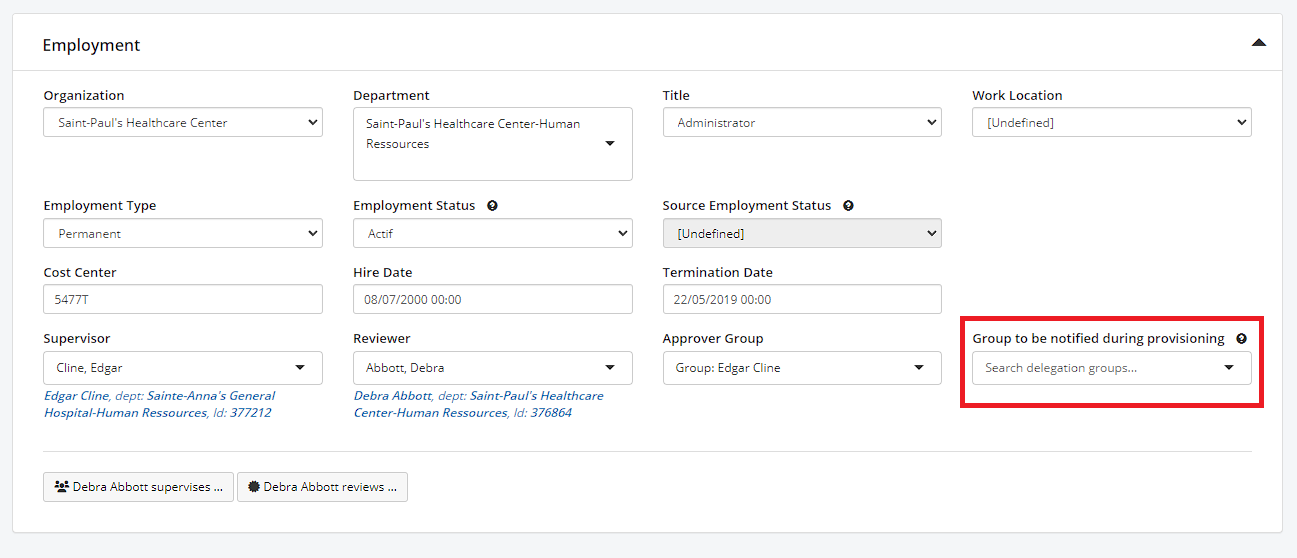
Identity – Group to be notified during provisioning
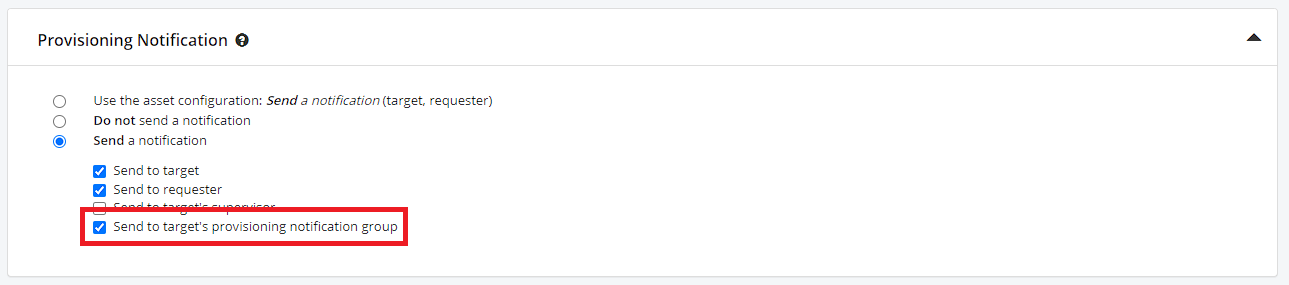
- In Asset Grouping, go to the “Provisioning” section and in the “Notification” zone, select “Send to target’s provisioning notification group”
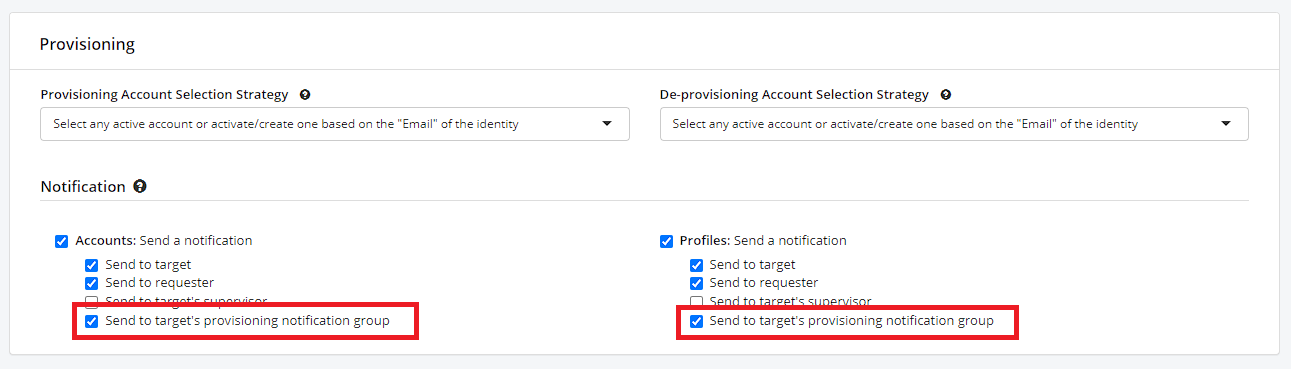
Asset Grouping – Group to be notified during provisioning
- In Asset, go to the “Provisioning” section, in the “Notification” zone activate “Send a notification” and choose “Send to target’s provisioning notification group “.
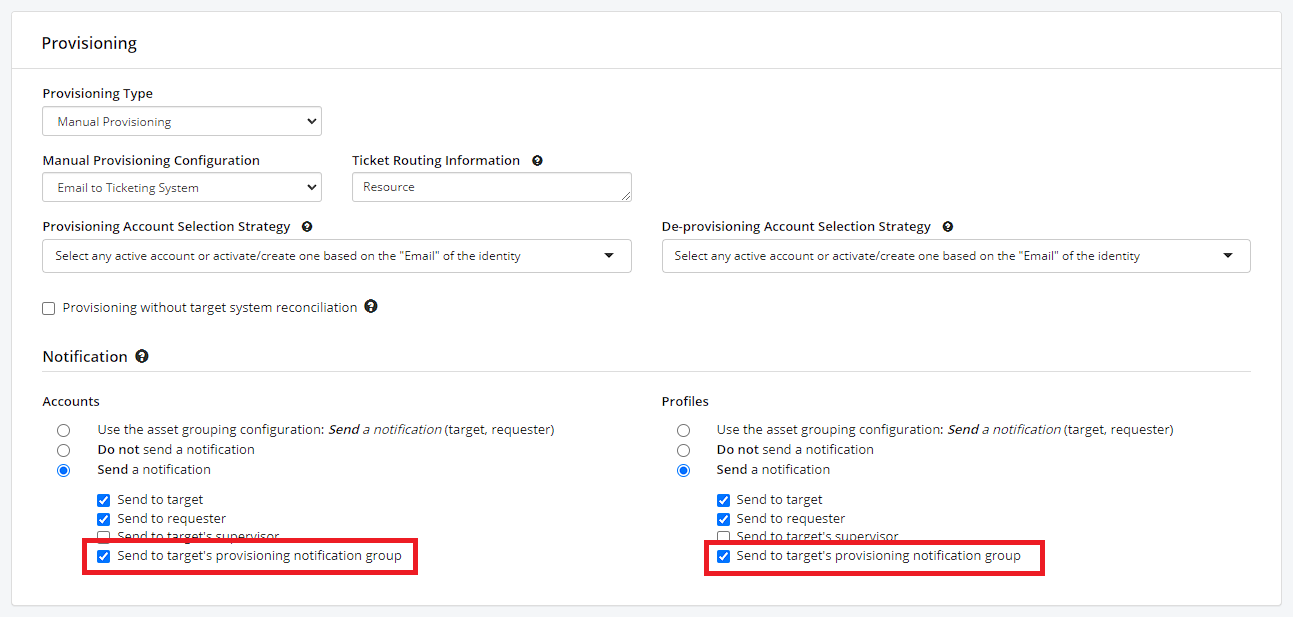
Asset – Group to be notified during provisioning
- In group, go to the “Provisioning notification” section, activate “Send a notification” and choose “Send to target’s provisioning notification group”.
Group – Group to be notified during provisioning
Connectors
- The following connectors have been added :
- SAP/Serrala (Via the SCIM-Connector connector ) (#3292).
- GLPI (#3680). See the documentation.
- Generic scripted API connector. See the documentation.
- A generic connector that can be customized using Groovy scripts has been added. This has the advantage of making it easier to create connectors without having to update the solution.
- A Groovy script management screen has also been added for creating, modifying or deleting scripts.
- The following script has been created for this connector:
- Workday (#3612). See the documentation.
IMPROVEMENTS
- Added the ability to configure the questions asked and possible answers when requesting identity termination via self-service (#3727). See the documentation.
- Sequence start-up activities (via Quartz) are now audited for better traceability (#3690).
- An email retry process has been introduced to address technical issues independent of RAC/M Identity (#3692). See the documentation.
- RAC/M Identity now supports the ability to configure multiple applications for SAML and Kerberos authentication. The account will be searched in each application in the order specified (#3718).
- These applications are configured via the following two fields in the config.properties file :
- auth.saml.app.id. The internal RAC/M Identity identifier of the application in which to search for accounts authenticated via SAML. There may be several identifiers separated by commas. In this case, they will be searched in order until the account is found. ex : auth.saml.app.id=9,25
- active.directory.application.id. The internal RAC/M Identity identifier of the application to be searched for Kerberos authenticated accounts. This can be a single identifier or a comma-separated list of identifiers.
- These applications are configured via the following two fields in the config.properties file :
- A configuration has been added to the config.properties file to enable or disable the ability to make requests concerning technical accounts (#3724). This feature can be configured using this line:
- self.service.allow_request_for_technical_account=true
FIXES
- We have corrected a problem with the account provisioning list screen. Under certain conditions, no accounts were displayed, preventing access to the details of these provisioning requests(#3709).
- When duplicating a role version, members were lost when saved. This has been corrected (#3625).










