
RAC/M Identity™ is our simple and effective identity governance (IGS) solution that enables large and small enterprises to understand and manage the complex relationships between users and their access to physical and digital resources, on-premise or SaaS.
Major enhancements
Activation of accounts via self-service.
We’ve added a new screen in the self-service section for account activation requests. To access it, simply use the corresponding tile in self-service.

Once on this screen, you’ll be able to request account activation. This gives users greater autonomy by allowing them to manage account activation requests themselves. (#3735)
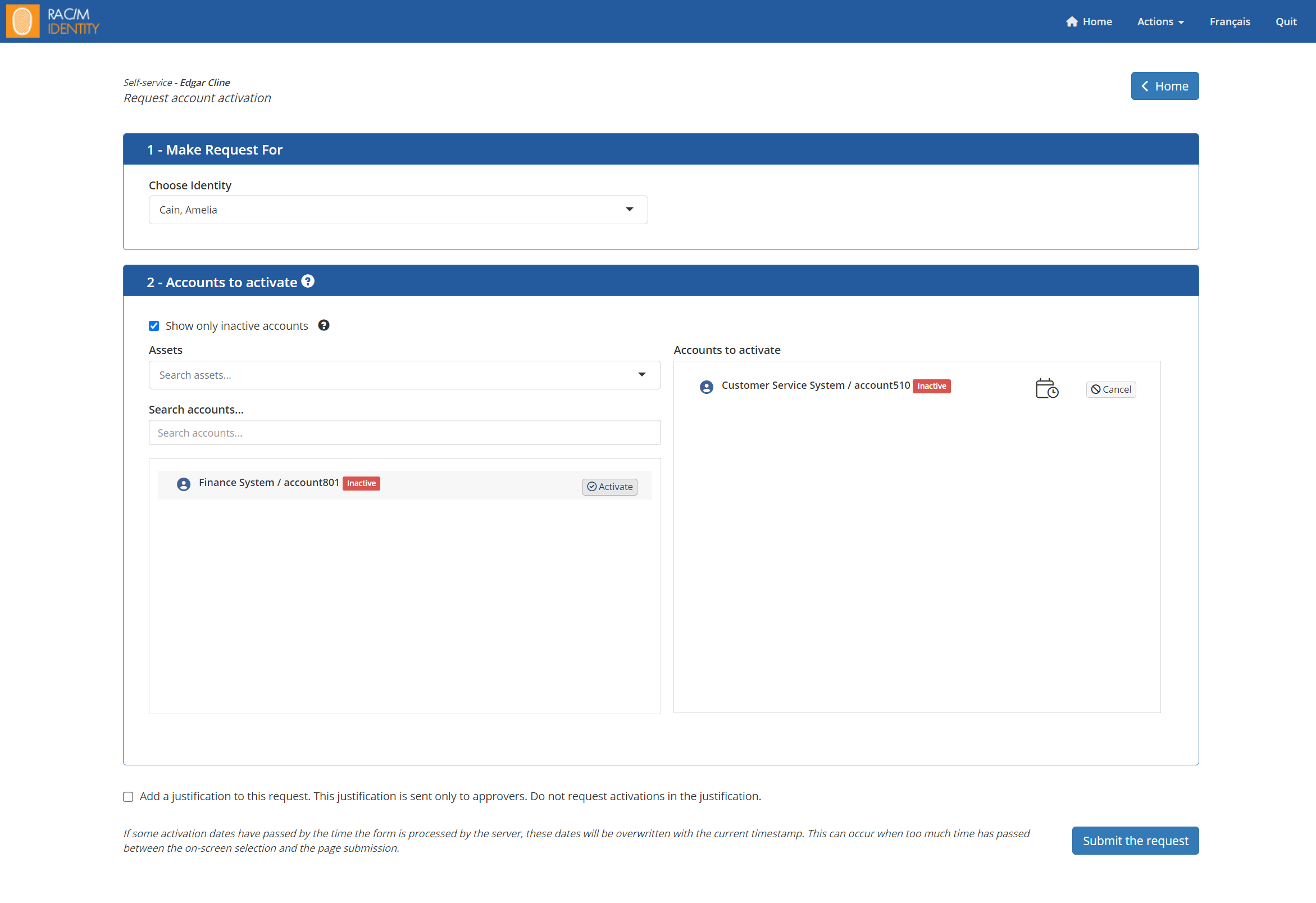
All workflow approval processes have been adjusted to support this new type of request. #3735
- The configuration self.service.new_request_account_activation.enable (from the config.properties file) enables or disables the functionality. “True” (enabled) or “false” (disabled).
- A new permission Account Activation Request has been added to manage granular access to the page by self-service users. By default, this permission is not given to any role.
In addition, a new button is now available in the account details screen of the admin console to activate the account. This activation is done without approval. #3883
Consolidation of notification emails for account and group provisioning. #3841
We’ve made changes to improve the efficiency of sending provisioning notifications. Automated provisioning emails are now consolidated by recipient and target. This means that all associated requests are grouped together in a single email, reducing the number of emails received by users. Emails are now sent asynchronously, enabling more efficient processing of requests.
Here’s an example of such an e-mail:
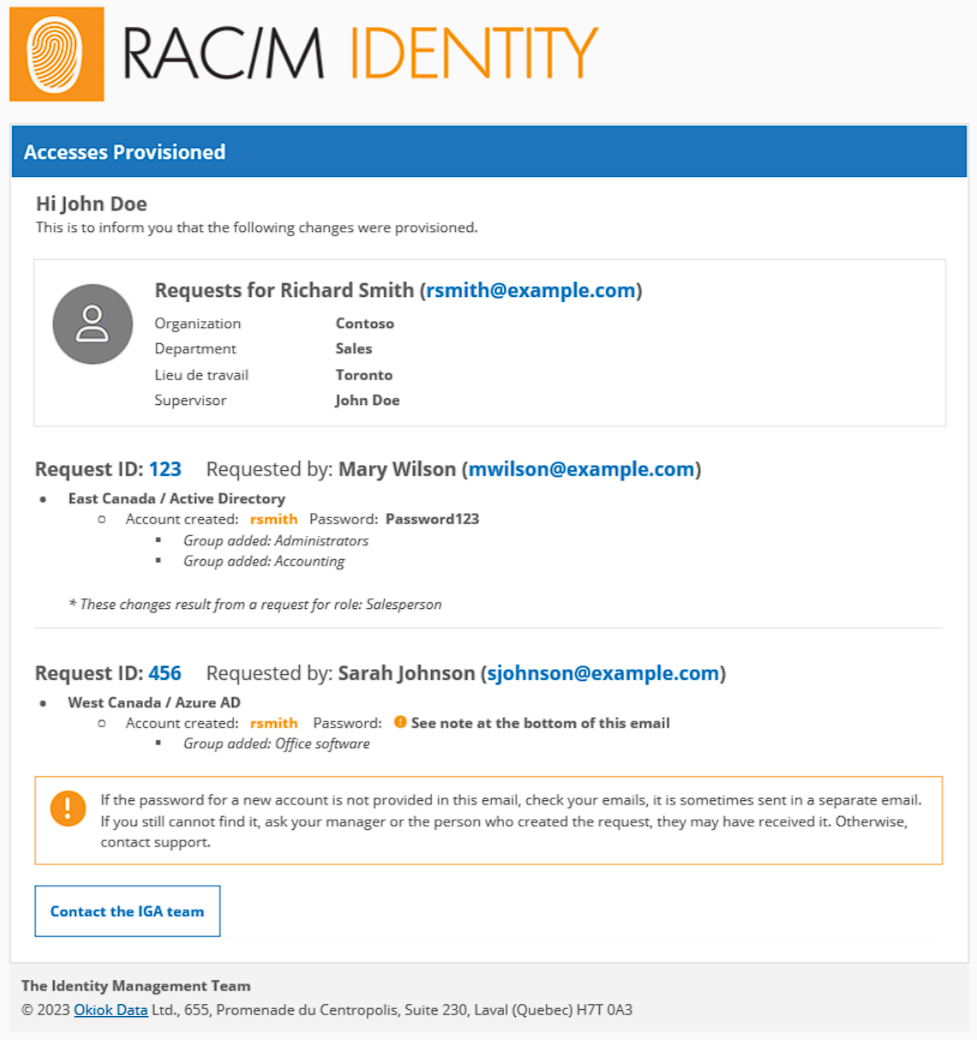
ATTENTION: This change modifies the application’s previous behavior in sending provisioning notifications.
It is essential to adapt these email template changes to ensure proper operation of RAC/M Identity.
- The automaticProvisioning_accesses.html template has been modified to support consolidation. It is necessary to replace the current template in your environment with this one.
- The automaticProvisioning_account.html template has been removed.
- The automaticProvisioning_password.html template has been added to allow passwords to be sent via an email independent of the notification email. This latter template is used in cases where the configuration requires the password to be sent in a separate e-mail.
Group and asset interfaces have been modified to bring more granularity to the sending of provisioning emails.
Here’s the notification configuration section for assets.
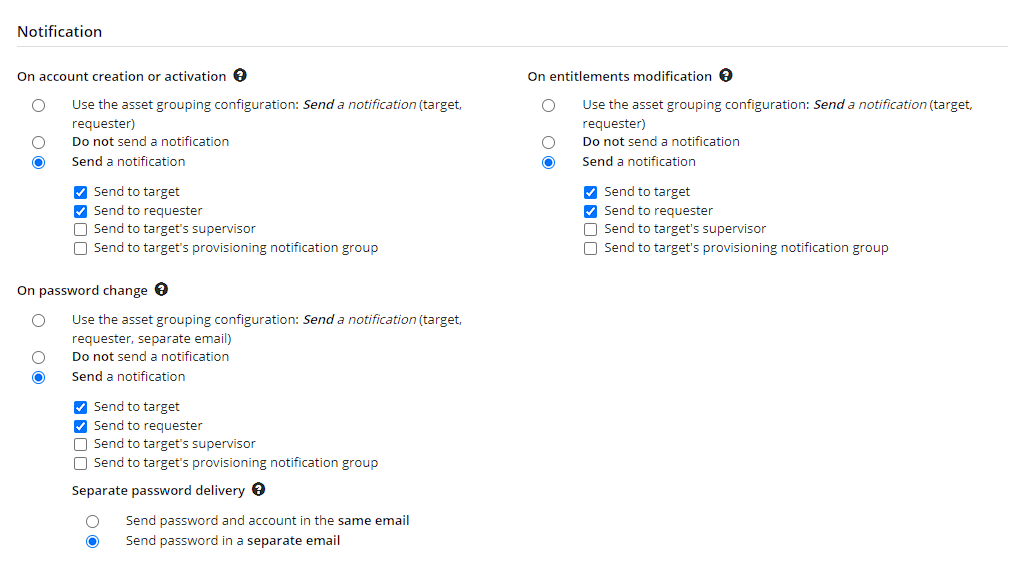
The following config.properties parameters are used to manage consolidated emails:
- mail.consolidation.job.enabled to enable the consolidation job.
- mail.consolidation.job.quartz the frequency at which pending emails are checked.
- mail.consolidation.min.delay.seconds for the minimum delay before sending and mail.consolidation.max.delay.seconds for the maximum delay before sending.
See the documentation for more details on configuring these notifications.
ENHANCEMENTS
- Updated “Scripted Api” connector (version 1.7) to support the following new connectors:
- SAP Success Factor #3407
- Ultipro UKG Pro #3294
- For more information, see documentation
- It is now possible to configure the job type(s) that determine the identities for which it is possible to make a termination request with the “Employment termination (employee)” tile. #3916
- The self.service.terminate_identity.hr_types configuration (from the config.properties) is used to configure the “HR identifiers” of the desired job types.
- This configuration is optional, if not specified, the default value is “external”.
- An empty value indicates that all identities can be selected.
- To configure multiple types, the “;” character is used as a separator.
- The self.service.terminate_identity.hr_types configuration (from the config.properties) is used to configure the “HR identifiers” of the desired job types.
- It is now possible to configure whether employment termination requests are automatically approved. #3918
- The mandatory config.properties file properties are:
- self.service.workflow.terminate_external_identity.auto_approved. “true” (enabled) or “false” (disabled).
- self.service.workflow.terminate_identity.auto_approved. “true” (enabled) or “false” (disabled).
- The mandatory config.properties file properties are:
- The JDBC driver for the SQL Server database connector is now included in the solution. In addition, all additional libraries required to authenticate with Azure AD and other authentication mechanisms supported by this Driver are also included.
- Audits added for import and export actions. #3829
- A feature to display inactive members of a dynamic role has been integrated into the roles screen. A checkbox has been added to this screen to filter only active members. This box is checked by default. #3892
- Added HTTP security header for X-Content-Type-Options. #3898
- Added empty descriptions for modules with no description. #3678
- Better handling of long descriptions in provisioning screens. #3684
- A mechanism was added to prevent a background process from executing before the end of the previous execution of the same process. #3860
- Added work location information to identity drop-down list. #3920
BUG FIXES
- Fixed a potential error that could occur when closing a campaign. #3687
- Fixed an SQL query error when there are more than 2100 identities when activating a role. #3893
- Fixed column width in delegation group list screen. #3614
- Fixed a problem displaying the execution history of a sequence when it contains special characters. #3852
- Fixed a problem with the alphabetical order in the list of audit filters when the language is French. Previously, the order did not take accents into account. The problem is now solved by ensuring that accents are taken into account during the alphabetical filter ordering process. #3286
- Fixed a formatting issue when exporting sequence results, causing incorrectly formatted CSV files with line breaks in comments. #3808
- Fixed a problem allowing users without read permissions to be able to view the list of access review campaigns on the self-service screen. #3807
- Fixed an issue where creating a module with the same name as another, but with spaces added, did not trigger an error. #3911
- Fixed an issue that occurred when creating a delegation group. #3805
- Fixed an issue where the login page was crashing because page elements were not loaded completely before being used. #3283
- Fixed the installation software to use data entered during a new installation. #3886
- Fixed an issue with the paging of a role version’s dynamic member list; the paging was taking into account all members rather than just the dynamic members. #2751
- Fixed the contextual description information in sequence execution. #3332
- Fixed an issue that prevented an end date from being selected in the various self-service requests when the `self.service.new.external.identity.end.date.enabled` parameter is set to “false” #3927
Breaking changes
- Because of the email consolidation feature, it is necessary to adapt email templates to ensure proper operation of RAC/M Identity.
Please see upgrade steps to version 3.18.0










