
S-Filer Portal™ is a complete solution that enables large and small organizations to meet all of their enterprise needs for secure file transfer and storage.
OKIOK RELEASES VERSION 4.18.0 OF S-FILER/PORTAL™ SECURE TRANSFER SOLUTION
New features
Azure AD adoption support
This new feature makes it possible to adopt users located in Azure AD. Prior to the introduction of this feature, it was only possible to adopt users located in an internal Active Directory. This configuration is carried out in the solution’s administration console. You can consult the section on Azure AD adoption in the official documentation here :
Configuring a new Microsoft Azure authentication mechanism
Enhanced solution usage statistics
Transfer statistics have been enhanced to include data on transfer volume and storage space. This data is available via the web interface and the REST API. Previously, only the number of transfers appeared in this screen. The solution usage statistics screen is accessible to system administrators. Data is updated automatically every hour.
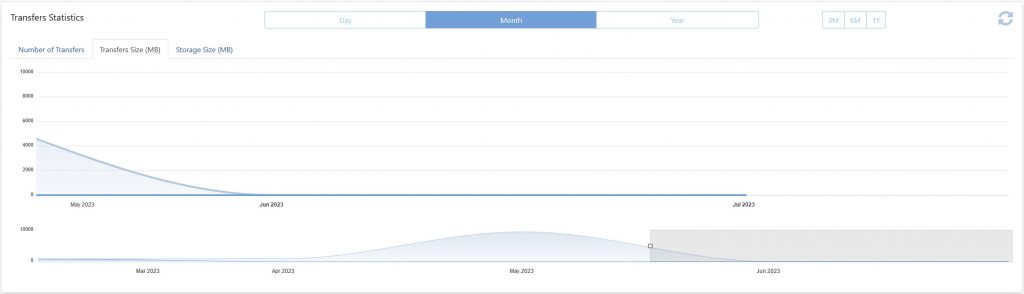
Transfer Statistics
These new statistics are also available via the solution’s REST API.
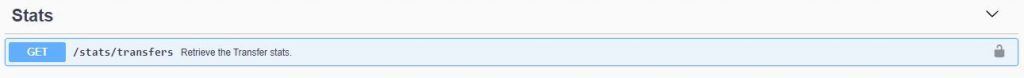
Transfer Statistics via the REST API
The result of this call to the REST API will be similar to :
{
'dataTruncated': true,
'transferStats': [
{
'year': 0,
'month': 'JANUARY',
'day': 0,
'hour': 0,
'downloadCount': 0,
'uploadCount': 0,
'downloadSize': 0,
'uploadSize': 0,
'totalStorageSize': 0
}
]
}Self-assignment of group members to a community
The aim of this new feature is to simplify the process of assigning users to different communities. Previously, the standard process for assigning users was as follows:
1. Create a community.
2. Create a group.
3. Assign a group to a community.
4. Create user.
5. Assign user to group.
6. Assign user to community.
The new process allows you to skip step 6. When assigning the group to the community in step 3, we can specify that all group members will automatically be assigned to the community. A new checkbox lets you specify whether the group should operate in automatic assignment mode or not.
This is very useful when combined with the group adoption feature where AD or Azure AD accounts are imported with their groups. This allows managing S-Filer communities membership entirely using AD or Azure AD.
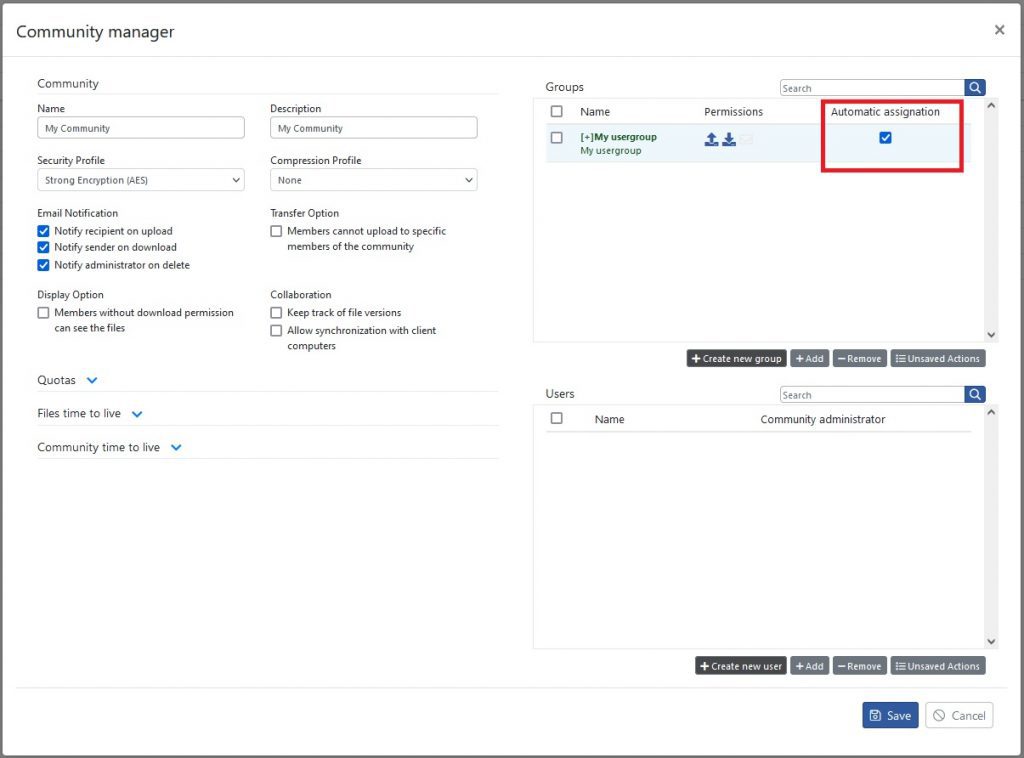
Self-assignment of group members to a community
You can consult the section on Community User Assignation in the official documentation here :
Automatically assign users to communities
Using the certificate manager to store ICAPS certificates
This new feature enables ICAPS certificates to be stored in the certificate manager. ICAPS is the protocol used by antivirus software to scan files. Before this feature was introduced, it was necessary to install the certificate in the server JVM “cacerts” truststore.
Certificate trust without server restart
It is now possible to trust a certificate without having to restart the S-Filer Portal server. When establishing a connection to a third-party system, S-Filer Portal will store the certificate in the “Unknown certificates” section of the certificate manager. In order to enable connectivity to these third-party systems, it is necessary to trust an unknown certificate. Prior to the introduction of this feature, it was necessary to restart the server so that it could consider the certificate as trusted.
Simplified SAML configuration
SAML configuration in the administration console has been redesigned and simplified to enable authentication directly from the Office 365 interface. It is no longer necessary to automatically go through the solution’s authentication page to access the application. The introduction of this new functionality has made it possible to remove the “Reply URL” configuration parameter from the SAML configuration. You can consult the section on SAML in the official documentation here :
SAML configuration with Azure AD
Transfer via a group identity
It is possible to upload a file under the identity of a group rather than under the identity of a user. This function is useful when the recipient of the file has no interest in knowing the user who initiated the transfer. For example, a “help desk” communicating with a recipient. In this case, it is not necessary for the recipient to know the identity of the help desk user.
This functionality is implemented via user groups. A user group now has an attribute enabling it to be identified by recipients. By default, this feature is not activated. It is therefore necessary to check the box to activate it and specify the name that should appear for the various notifications. Only system and group administrators have access to this attribute. The screenshot above shows where configuration takes place:
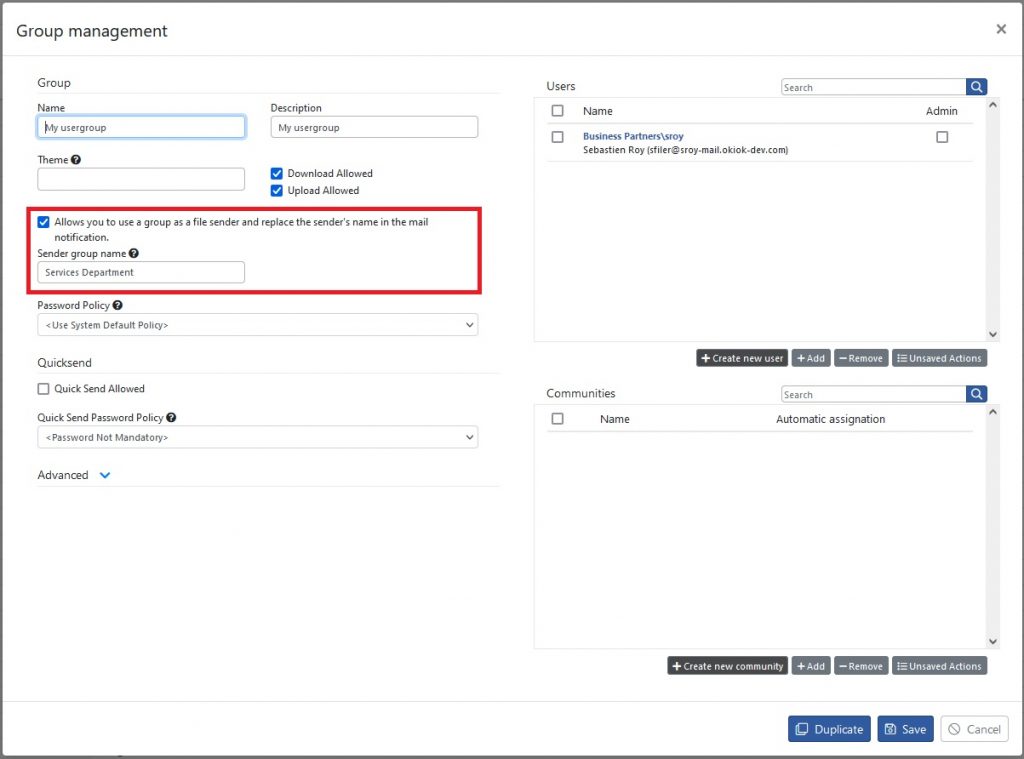
Group identity configuration
Then, when it comes to performing a transfer, users belonging to a group with this configuration will have to specify under which identity they wish to perform the transfer. By default, transfers are carried out under the user’s identity.
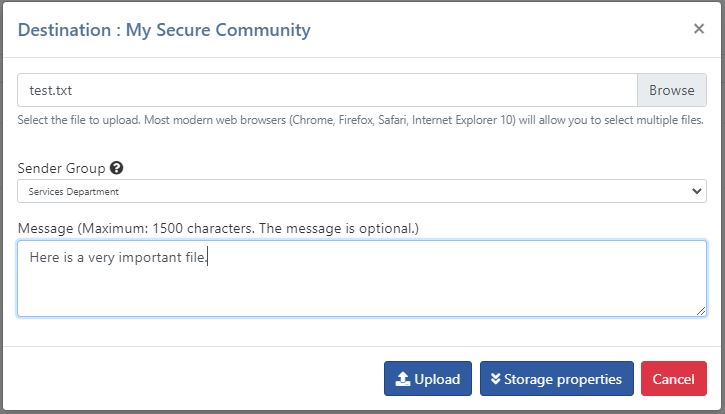
Transfer via a group identity
Fixes
- Improved error handling for community quota management. This change is designed to give users more information when applying specific quotas to a community. A label provides information on the global settings that apply, guiding administrators.
- The user activity report has been modified to avoid truncating certain information.
- Corrected the process of deleting a group for which there was a restriction on the origin of the IP address. It was previously necessary to remove this restriction before deleting the group.
- Accented characters are now ignored when searching in the navigation tree on the left of the interface.
- The Administrative Console “Scheduler” was corrected to prevent simultaneous execution of two identical tasks.
- Modification of the encryption algorithm to use AES256-CTR rather than AES256-CBC to comply with the highest security standards.
This upgrade requires an update of the database. We strongly recommend that you perform a full backup of the solution prior to the upgrade. Do not hesitate to contact our support group if you have any questions regarding this upgrade at support@okiok.com










